I mentioned you how to share a folder and how to assign permissions to users in a shared folder in my essay on NTFS (Security Permissions) and Sharing Permissions in Windows Server 2019 Part-1.
I will mention about NTFS Security Permissions (Security Permissions & NTFS Permissions) in Windows Server 2019 as the second part of my essay, and mention about how you can assign permissions to users in a shared folder in this essay.
The term of Permission is a set of authorizations that determine what the access level assigned to the user or group on resources such as folders and files. For example, while a user is given Read Permission on a shared folder, another user can be given both Read Permission and Write Permission on a shared folder. In short; You can provide which user or user group permissions on a shared folder with Permissions, and arrange the authorizations of users or groups on these folders.
Permission Types on File Server
1- Sharing Permissions
2- Security Permissions (NTFS-New Technology File System Permissions)
NOTE 1: My essay consists of 2 parts; Part 2 is the one about Security Permissions (NTFS Permissions) that you are reading now.
2- Security Permissions (NTFS Permissions)
I have seen that the permission configurations in both Sharing and Security Tabs are intermingled with each other both in the companies I have provided consultancy and in my IT trainings I provide by my students. The Security Permissions (NTFS Permissions) is an essential authorization field for the permission configuration process on a folder, whether you share a folder or not.
To clarify the explanation of "Whether share a folder or not"; With regard to Sharing Permissions, which I mentioned in the 1st part of my essay, you need Sharing Permissions when you access a folder through UNC (Universal Naming Convention), over Network. However, Sharing Permissions alone are not enough here. If you do not assign permissions on the Security Tab, you will never be able to access that folder. Because the main permission area of the folder is the permissions on the Security Tab, and when the user accesses the folder, the permissions in both Sharing and Security Tabs are checked and the most restrictive one is applied.
However, just the opposite; If you do not need to access a folder through UNC (Universal Naming Convention), over the Network, that is, if you will only access the folder on the computer where the folder was created, then you do not need Sharing Permissions in the Sharing Tab, just click the Security Tab. It will be sufficient to assign permissions on it.
In summary;
• If the shared folder is accessed over the Network, both Sharing Permission and Security Permission are actually compared, and the permissions on both sides are compared and the most restrictive one is applied.
• If the shared folder is accessed from the computer on which the sharing is opened, Sharing Permission will not be valid. Only NTFS Security Permission is valid and no comparison is made between them.
NTFS (New Technology File System) Permissions
NTFS (New Technology File System) Permissions Table is as follows. Permissions can be divided into 2 sections.
These are;
1- Basic Permissions
There are 6 Basic Permission.
2- Advanced Permissions
There are 13 Advanced Permission based on 6 Basic Permission.
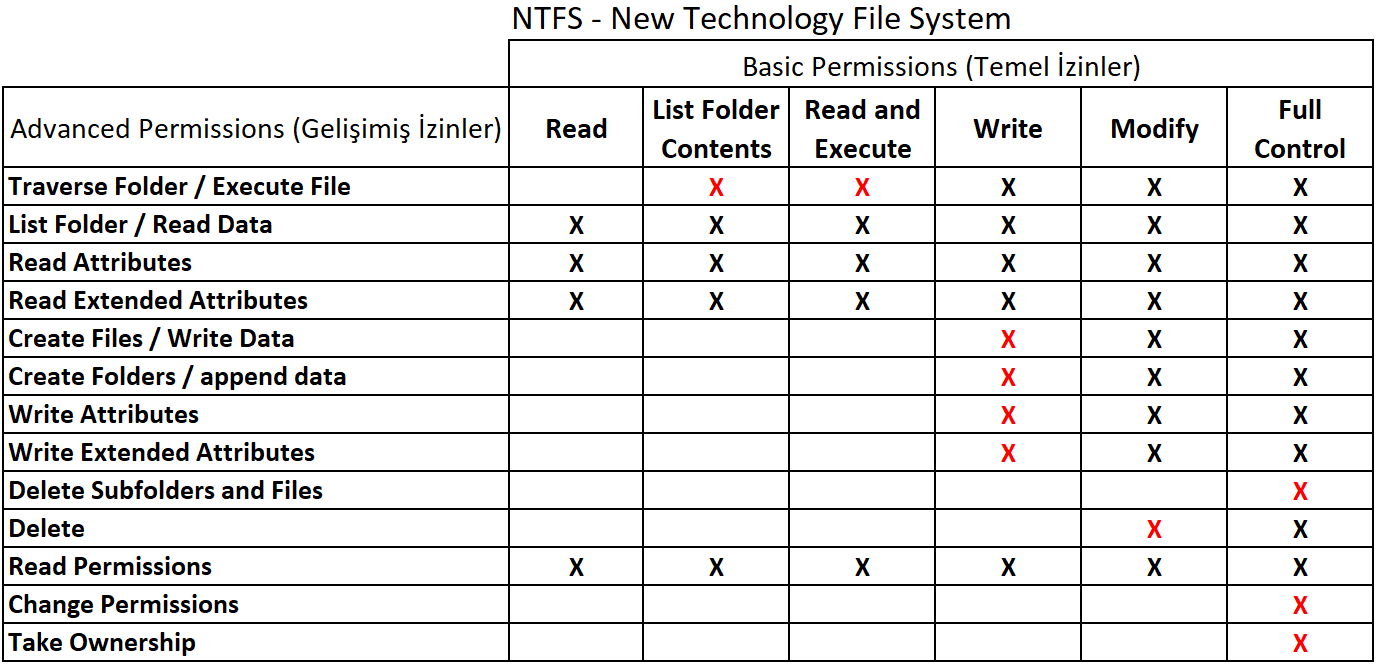
NOTE 2: The red signs in the table show which sub-authority an authorization covers additionally, in other words, which plus (+) property they contain. I will discuss the details later in my essay.
1- Basic Permissions
Basic Permissions are the main permissions to be given for a folder or a file. Each of these main permissions has sub-authorization details, which we call Advanced Permissions, and each basic permission has the corresponding advanced permission (Advanced Permission).
● Read: Listing files and subfolders in a folder.
● List Folder Contents: Listing files and subfolders in a folder.
NOTE 3: Although Read and List Folder Contents permissions appear to be practically identical to each other, there are serious differences between them.
The most important of these serious differences are as follows;
1- While you can view folder contents with both; it becomes possible to view only files in a folder, opening files and documents will not become possible with List Folder Contents.
In short, only the permission of List Folder Contents need to be selected in case of a demand such as only a folder content is allowed to be seen, but files cannot be opened.
2- Selection of the permission of Traverse Folder / Execute File, which comes with selection of the permission of List Folder Contents, I will mention in the following parts of my essay, is the Advanced Permissions.
● Read and Execute: Reading the file contents and running the files (Scripts, .exe extension etc. can be run).
NOTE 4: Selecting Read and Execute alone will automatically select Read and List Folder Contents permissions. Conversely, while all three Read and Execute, Read and List Folder Contents permissions are selected, only Read and Execute permission can be disabled.
NOTE 5: When a user or group is added to ACL (Access Control List) for authorization; Read, List Folder Contents, and Read and Execute permissions are selected by default.
● Write: Add files and folders.
NOTE 6: With the use of Write permission alone, you cannot change the names of existing or newly created files or folders while inside the permitted folder. This option can be used to move folders or files from another directory to a shared folder (with the permission) using Cut, Paste (paste) or Drag & Drop (drag & drop) method. However, you can add or delete any file while in the given folder.
Info!: You cannot delete with the use of Write permission alone.
● Modify: Creating, deleting, and modifying created folders, files, and subfolders.
● Full Control: Full control over the folder and its contents. In addition to the Modify permission with this full control right.
NOTE 7: In addition to the Modify permission, the Full Control permission gives 3 additional Advanced Permission permissions which are Change Permissions, Take Ownership, and Delete Subfolders and Files.
2- Advanced Permissions
Advanced permissions correspond to any of the basic permissions (Basic Permissions) I mentioned above as a group of a few. A detailed grouping has been made in the Basic Permissions & Advanced Permissions Provisions title, but first let's see all of them in a single list and examine the purpose of each of them.
● Traverse Folder / Execute File: Even if a user does not have permission to access a main folder, if he /she has permission to access subfolders, it is the permission that allows or denies the relevant user to gain access by typing the path to the relevant subfolder.
If there is any Executeable file such as script, .exe or .bat in a subfolder he /she can access with the permission of Execute File, it allows or denies the relevant user(s) to run these executable files.
● List Folder / Read Data: Allows or denies viewing the names of a folder and its subfolders and data in a file.
While List Folder is applied for folders, Read Data is applied for files.
● Read Attributes: Allows or denies viewing the properties of folders and files (such as Read only or Hidden properties).
● Read Extended Atributtes: Allows or denies viewing advanced features in files and folders.
● Create Files / Write Data: Read the comparison.
● Create Folders / Append Data: Read the comparison.
The Comparison of Create Files / Write Data & Create Folders / Append Data
Differences are shown in the following conditions:
When these two advanced permissions, which come into effect with the Write Basic Permission, are both selected at the same time, using the Write permission alone will be subject to the rule of "you cannot change the names of existing or newly created files or folders while inside the permitted folder" as I mentioned in NOTE 6.
However;
1- Only when Create files / write data is selected.
NOTE: Create folders / append data is not selected.
- A new file can be created.
- File names and extensions (.docx, .txt, .xlsx etc.) in the current file can be changed.
- Actions of deleting data within the current file content and adding data within the file, etc. cannot be done.
In addition;
- A new folder cannot be created.
- Name of the current folder cannot be changed.
- A new folder cannot be created.
2- Only when Create folders / append data is selected.
NOTE: Create files / write data is not selected.
- A new folder can be created.
- Name of the current folder can be changed.
In addition;
- A new file cannot be created.
- File names and extensions (.docx, .txt, .xlsx etc.) in the current file cannot be changed.
- Actions of deleting data within the current file content and adding data within the file, etc. cannot be done.
● Write Attributes: Allows or denies changing the properties of files and folders. This feature does not make changes to data in a file or folder, it only changes its properties (such as Read only or Hidden).
● Write Extended Attributes: Allows or denies changing the advanced properties of a file and folder. These features can be created by various programs.
● Delete: Allows or denies deletion of main folder (empty or with files inside) and folders under main folder (empty or with files inside) or only files (whether in main folder or subfolder) gives or hinders.
Info!: If the Delete permission is removed on files (on file basis) and these files are also located in subfolders under main folder, subfolders cannot be deleted with the Delete permission from a folder alone! Delete Sub Folder and Files permission is additionally required for this operation! However, it is worth noting that files in a sub-folder that do not have the Delete permission on file basis will be deleted from the relevant folder!
● Delete Sub Folder and Files: Allows or denies deletion of subfolders that contain files with the Delete permission removed on file basis.
● Read Permission: Allows or denies viewing permissions on folders and files.
● Change Permission: Allows or denies changing permissions on files and folders.
● Take OwnerShip: Allows or denies taking ownership of folders and files.
Provisions of Basic Permissions & Advanced Permissions
The list below lists which Basic Permission is selected and which Advanced Permission is automatically selected. So when you choose a Basic Permission; Advanced permissions based on this basic permission (Basic Permission) are selected automatically. In other words, each Basic Permission has the equivalent of several advanced permissions in a group. However, you have the opportunity to opt out of one or more of the advanced permissions selected as Basic Permission. In this case, Special Permissions will be activated, which I will go into detail in the following parts of my essay.
● With selection of Read Permission;
• List Folder / Read Data
• Read Attributes
• Read Extended Attributes
• Read Permissions
Ex. Suppose you remove the Read permission from the basic permissions (Advanced Permissions) that are automatically selected for a user or a group in a folder; In such a case, the information on who has which permissions on folders and files for the respective user or group becomes unreadable.
Warning! 1: If you remove one or both of the List Folder / Read Data and / or Read Attributes advanced permissions (Advanced Permissions), you will not be able to access the folder.
● With selection of List Folder Contents;
• Traverse Folder / Execute File *
• List Folder / Read Data
• Read Attributes
• Read Extended Attributes
Warning! 2: If you remove one or both of the List Folder / Read Data and / or Read Attributes Special permissions, you will not be able to access the relevant folder.
● With selection of Read Extended Attributes Permission;
• Traverse Folder / Execute File *
• List Folder / Read Data
• Read Attributes
• Read Extended Attributes
• Read Permissions
● With selection of Write Permission;
• Traverse Folder / Execute File
• List Folder / Read Data
• Read Attributes
• Read Extended Attributes
• Create Files / Write Data *
• Create Folders / Append Data *
• Write Attributes *
• Write Extended Attiributes *
• Read Permissions
● With selection of Modify Permission;
• Traverse Folder / Execute File
• List Folder / Read Data
• Read Attributes
• Read Extended Attributes
• Create Files / Write Data
• Create Folders / Append Data
• Write Attributes
• Write Extended Attiributes
• Delete *
• Read Permissions
NOTE 8: The only difference between Modify and Write is the Delete permission corresponding to the Advanced Permission.
● With selection of Full Control Permission;
• Traverse Folder / Execute File
• List Folder / Read Data
• Read Attributes
• Read Extended Attributes
• Create Files / Write Data
• Create Folders / Append Data
• Write Attributes
• Write Extended Attiributes
• Delete Subfolders and Files
• Delete
• Read Permissions
• Change Permissions *
• Take Ownership *
Application-1
As I mentioned at the beginning of my essay; Whether a resource is accessed over the Network (network) or the computer where the share is opened, it is absolutely necessary to assign Security (security-NTFS) permissions. At this point, if the shared folder is accessed over the Network (network), both Sharing Permission and Security Permission (security-NTFS permission) are actually compared, and the permissions on both sides are compared and the most restrictive one is applied. However, if the shared folder is accessed from the computer on which the share is opened, Sharing Permission will not be valid. Only Security Permission (security-NTFS permission) is valid and no comparison is made between them.
Since the folder authorization processes are mostly configured to access server-centric remotely through File Servers, access to the source is done through UNC (Universal Naming Convention) Path. At this point, it is necessary to set up both Sharing Permission (sharing permission) and Security Permission (security-NTFS permission) configuration strategy on the source folder.
At this point, based on my field experience, my personal recommendation would be to grant the maximum Change (for full control) authority for the Everyone user group in the Sharing Permission section and configure all restrictions on the side of Security Permission (security-NTFS permission). Because if the shared folder is accessed over the Network (network), both Sharing Permission and Security Permission (security-NTFS permission) are actually compared and the permissions on both sides are compared and the most restrictive one is applied.
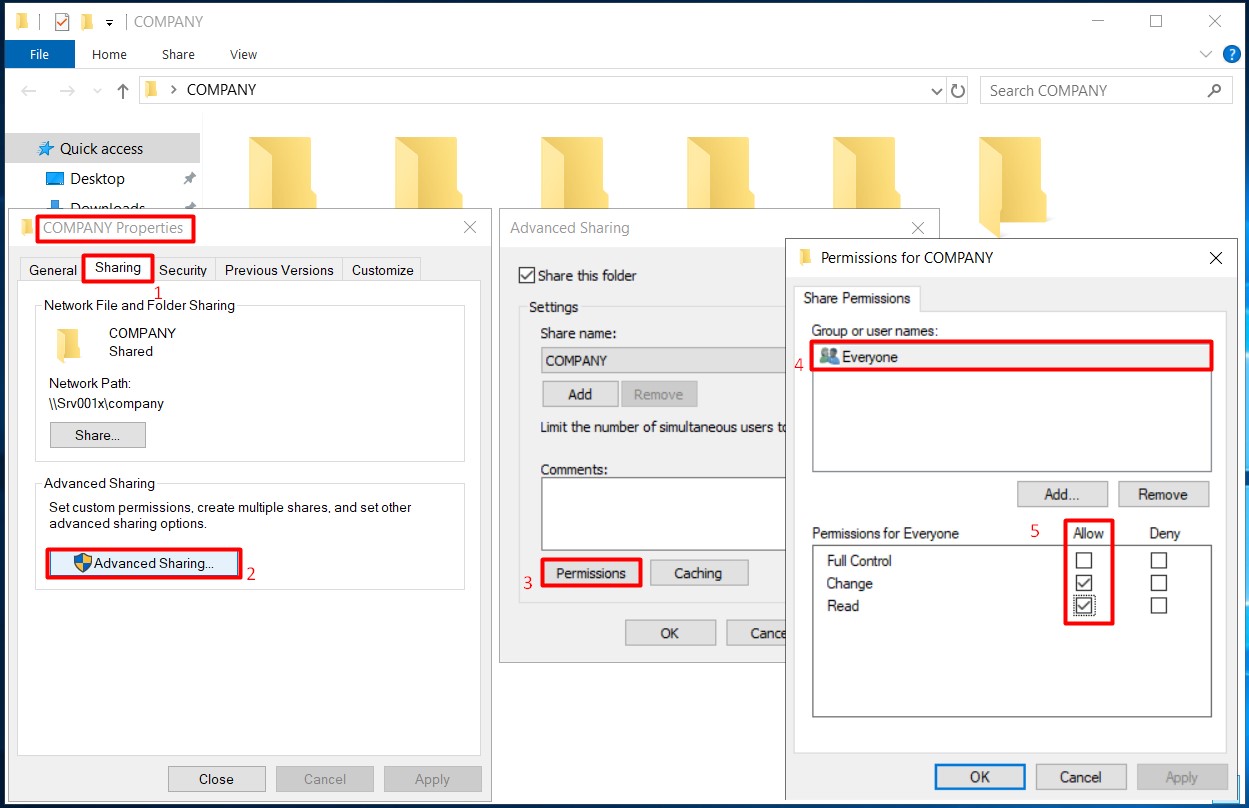
1- I am creating a folder named COMPANY on File Server and open this folder to share. When sharing, I am granting Change authority to the Everyone user group in the Allow section by clicking the Permissions button.
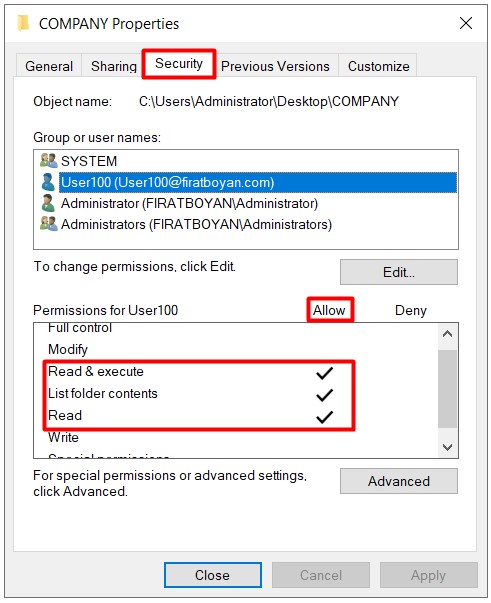
2- Now it is time to assign NTFS permissions in the COMPANY folder. In the Security Tab, Ex. I am granting Read authorization in Allow section for the user User100.
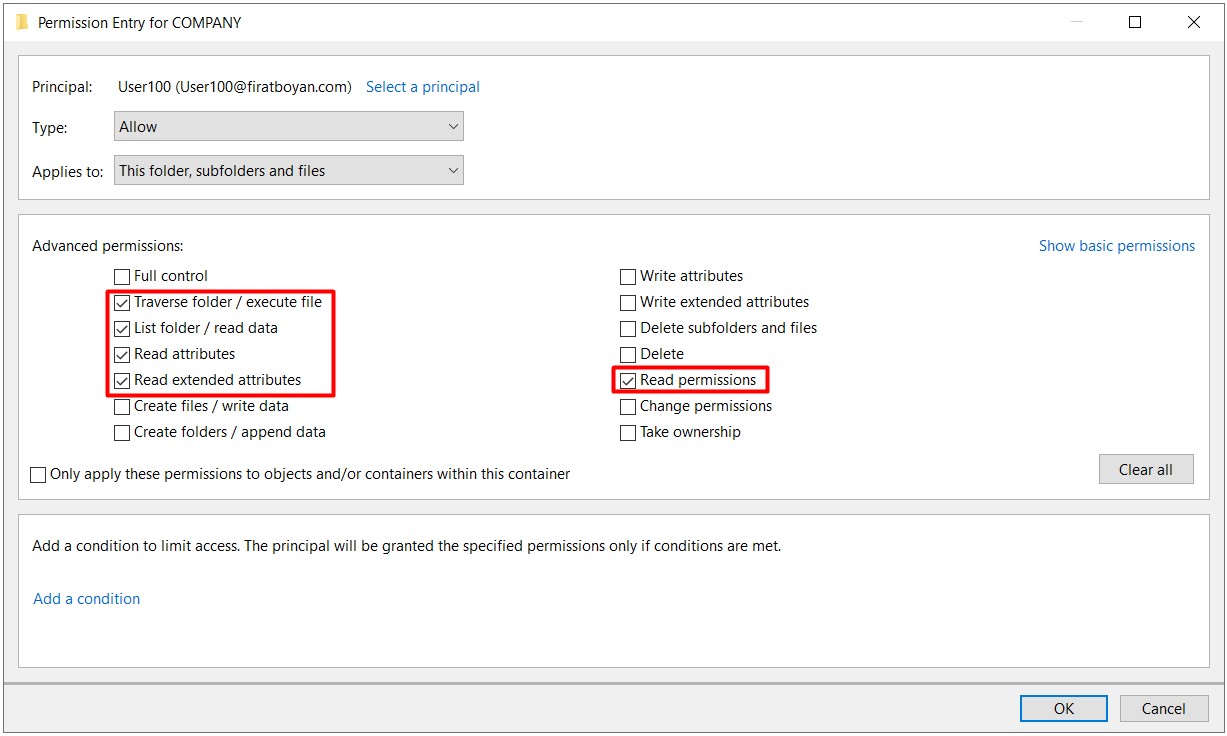
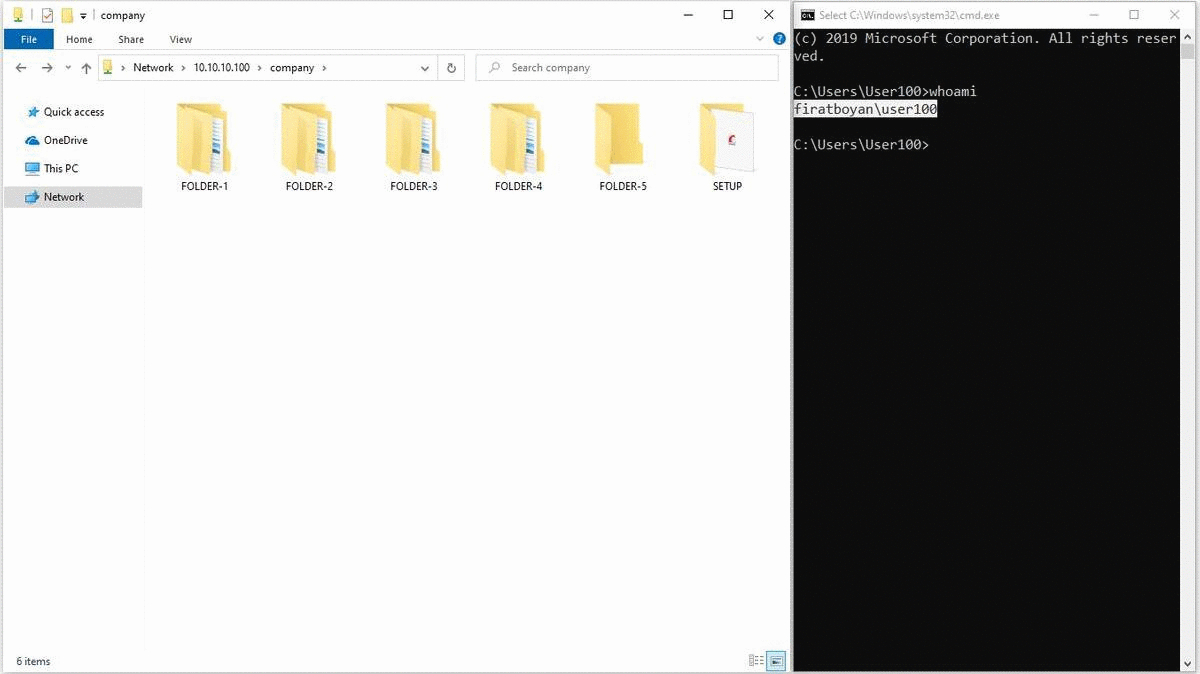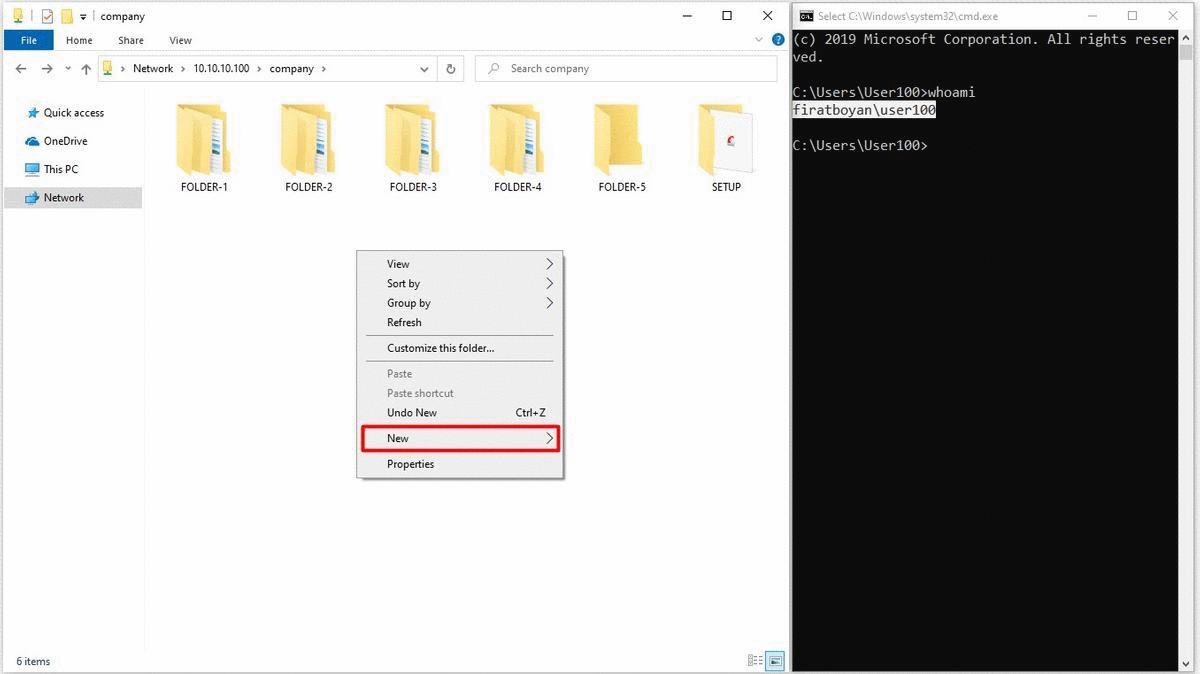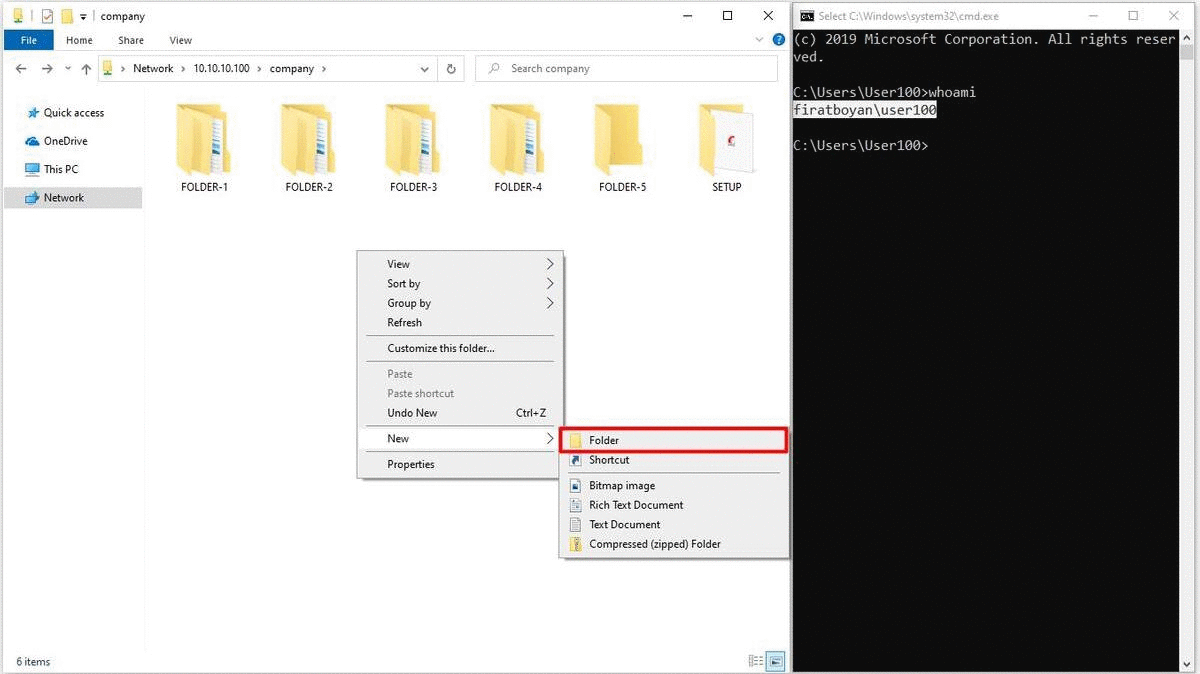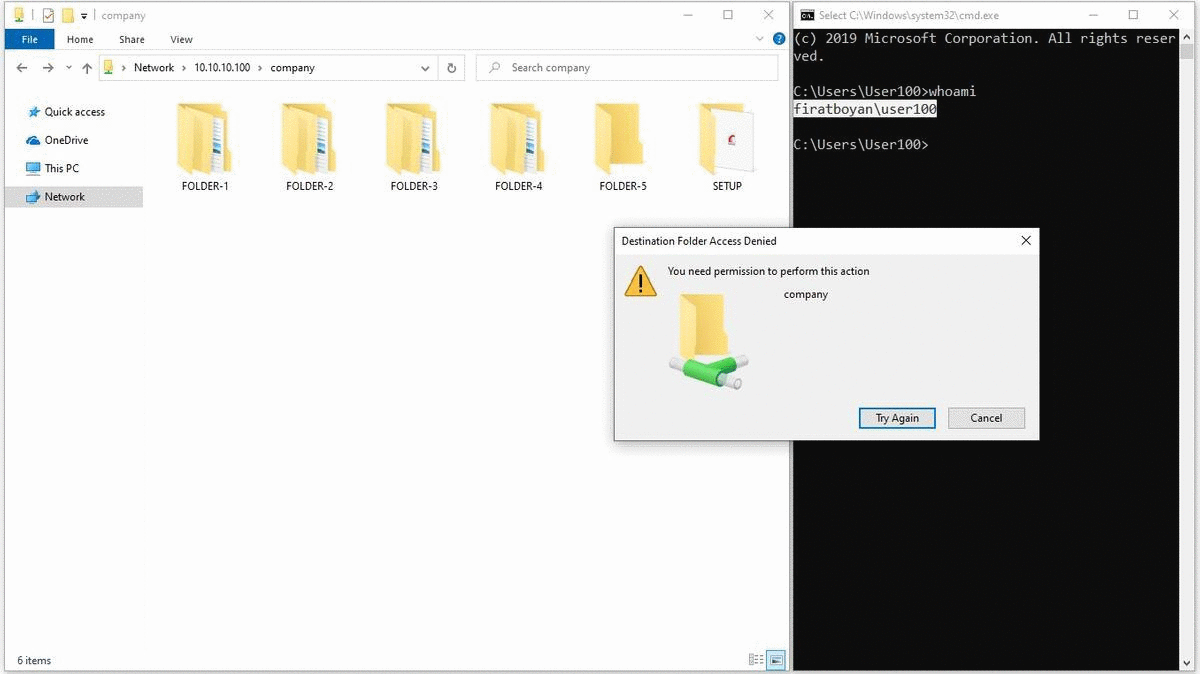
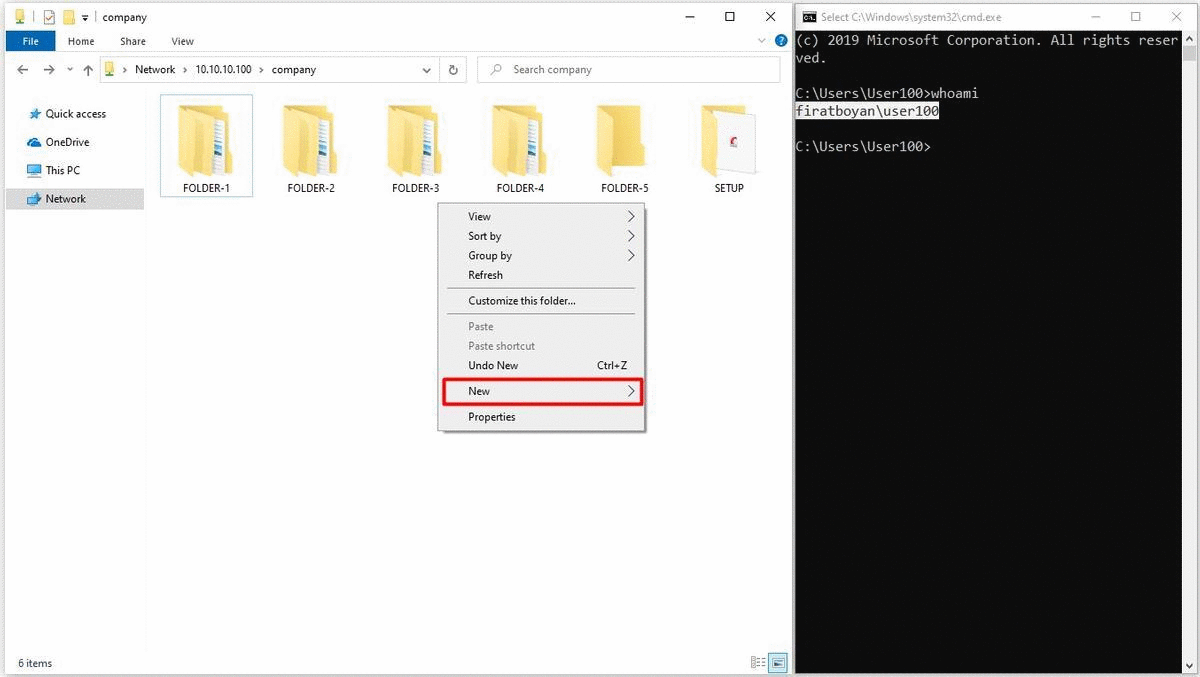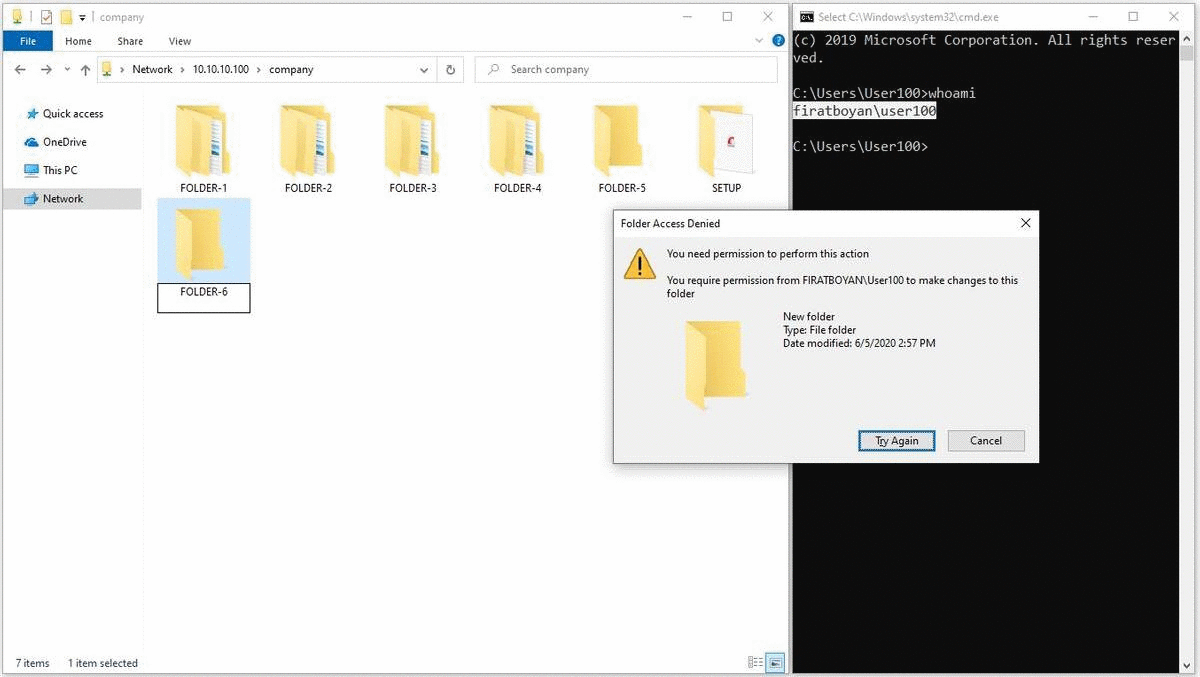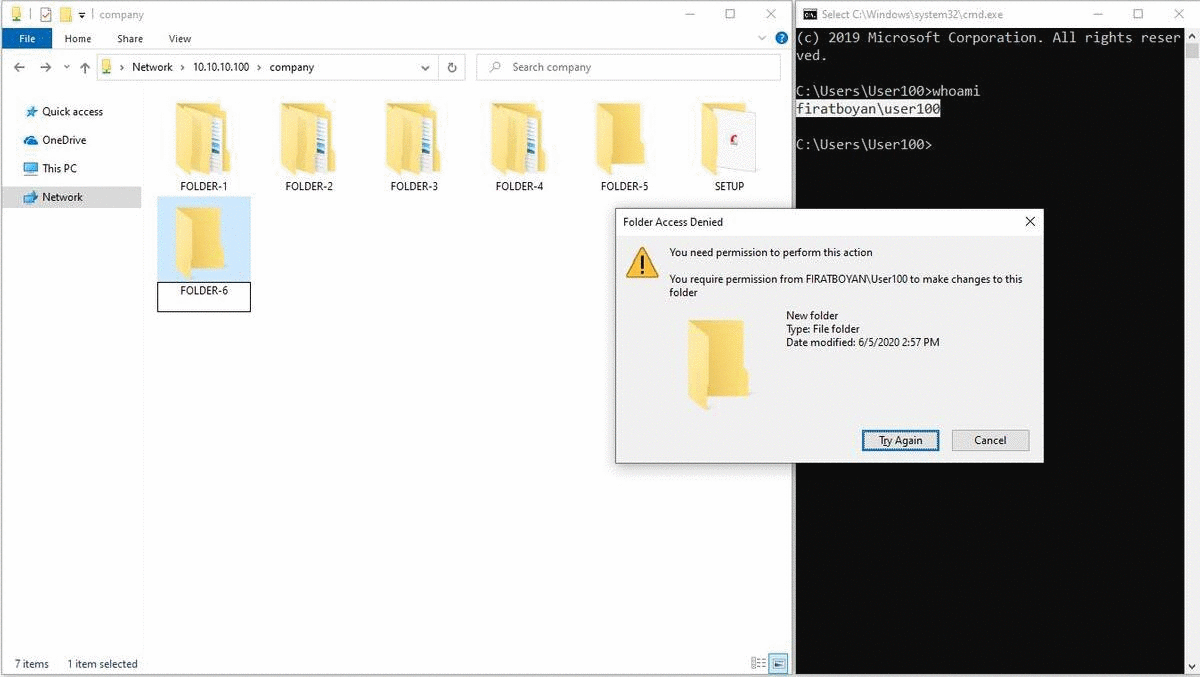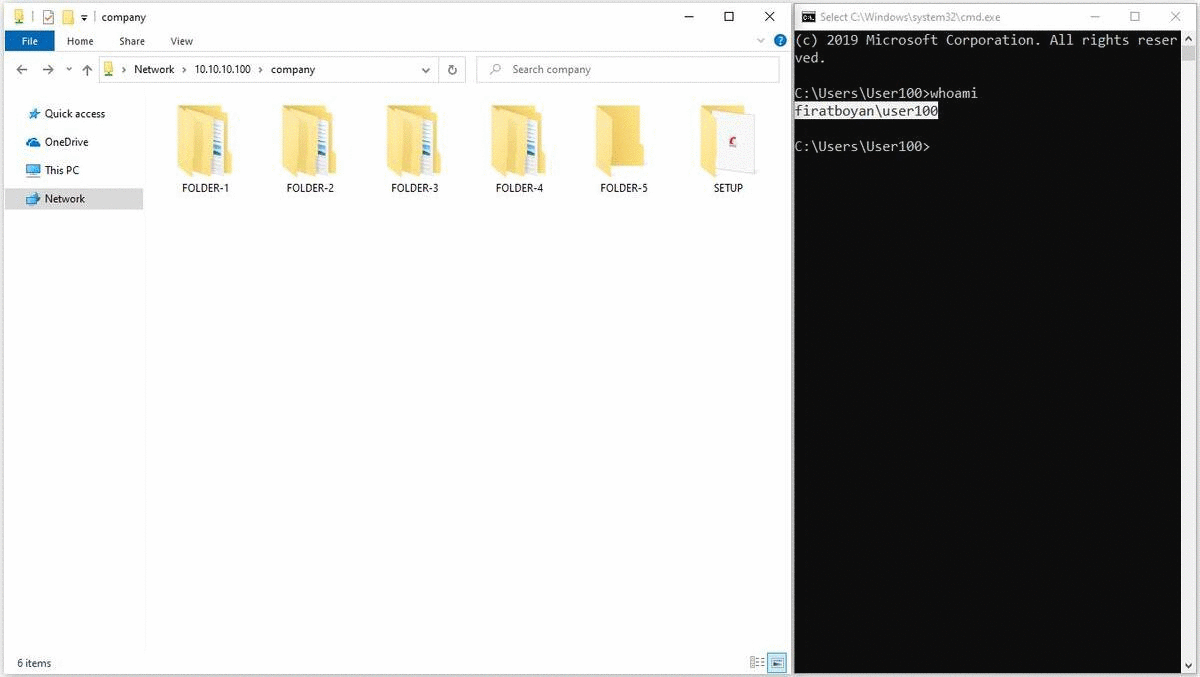
3- When I try to create a New Folder by accessing the share folder through UNC (Universal Naming Convention) Path from the Windows 10 operating system of the User100 user, I get a warning stating that I am not authorized to do this. Remember that I defined the Change authorization for the Everyone user group in the Sharing Permission section when sharing the COMPANY folder. So, I normally should be able to create folders, on the Security Permission side,but we can only perform reading since I granted only Read authorization and the most restrictive of the permissions on both sides is the Read authorization. "whatever is the most restrictive, it applies." This is the explanation for the statement.
Application-2
1- I am now updating the authorization level on the Security Permission side to Write for the same user, User100 in the same COMPANY folder.
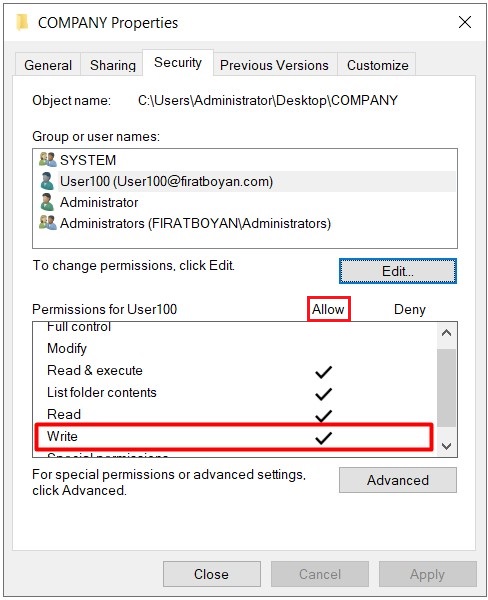
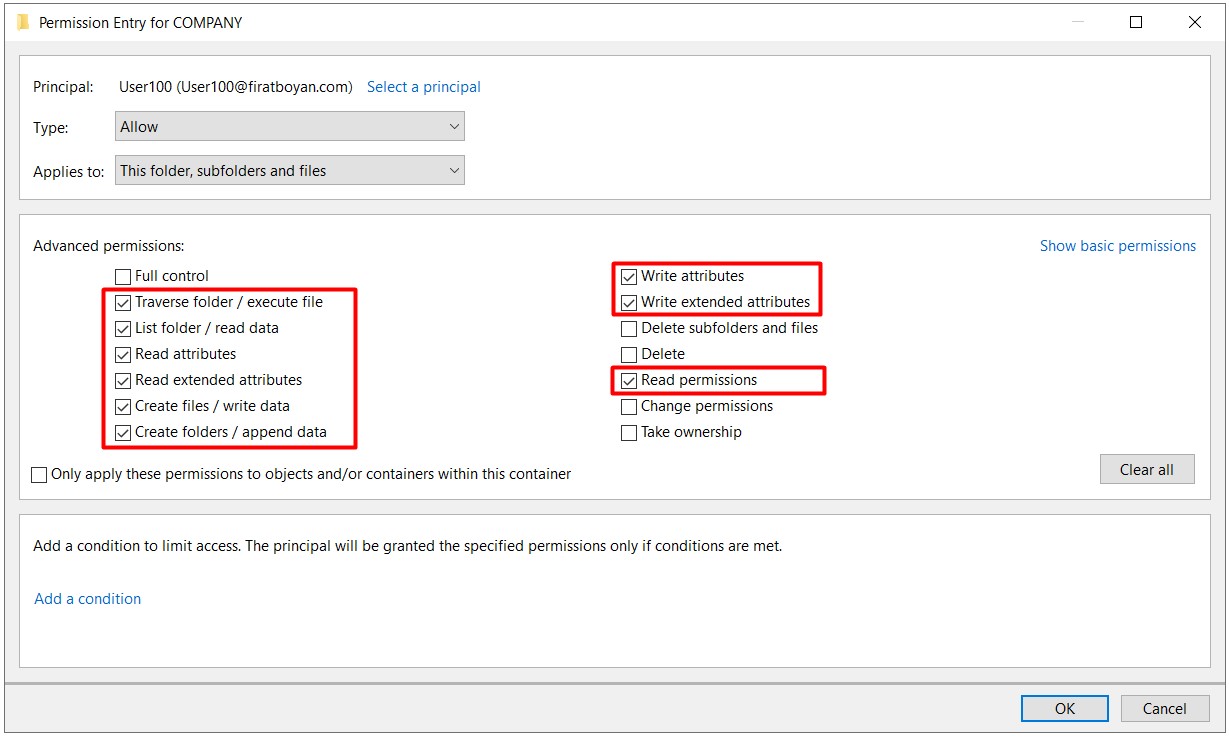
2- User100 is creating a New Folder by accessing the shared folder through UNC (Universal Naming Convention) Path from the his / her computer with Windows 10 operating system and when trying to change the folder name without clicking the Enter key or mouse click in the blank area, the user is getting a notification stating that he / she is not authorized to do this operation. Since a process such as a change of folder name is actually implemented as a Delete action and there is no Delete against the Write Basic Permission, we cannot perform this operation.
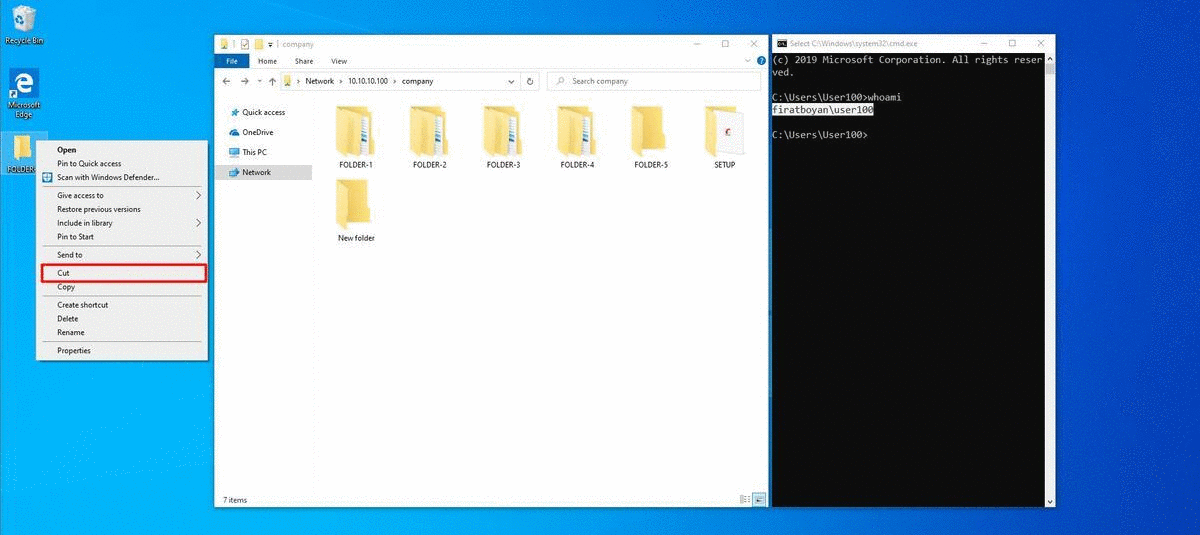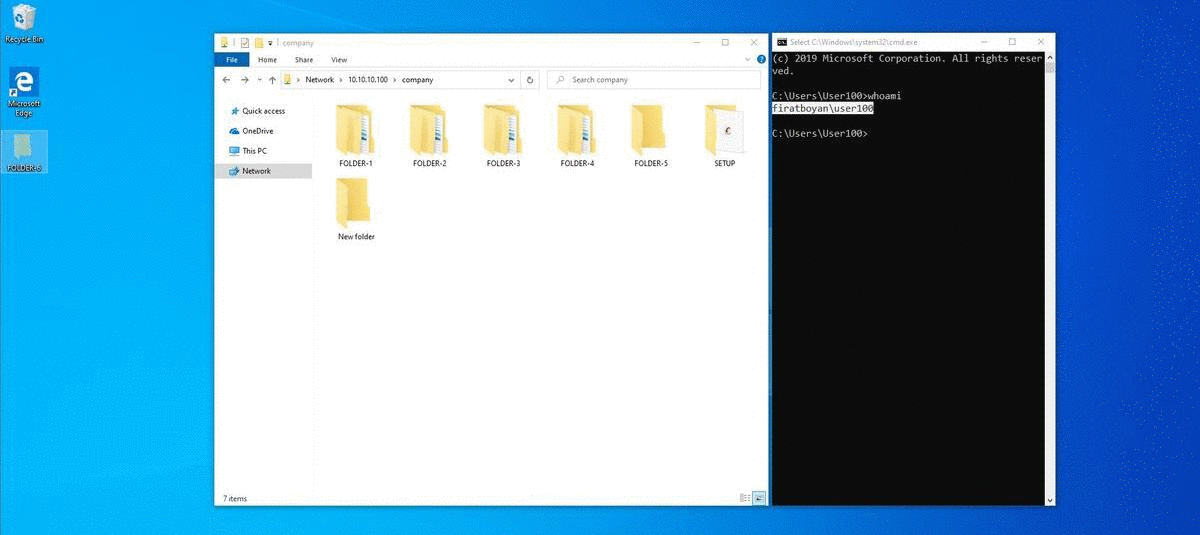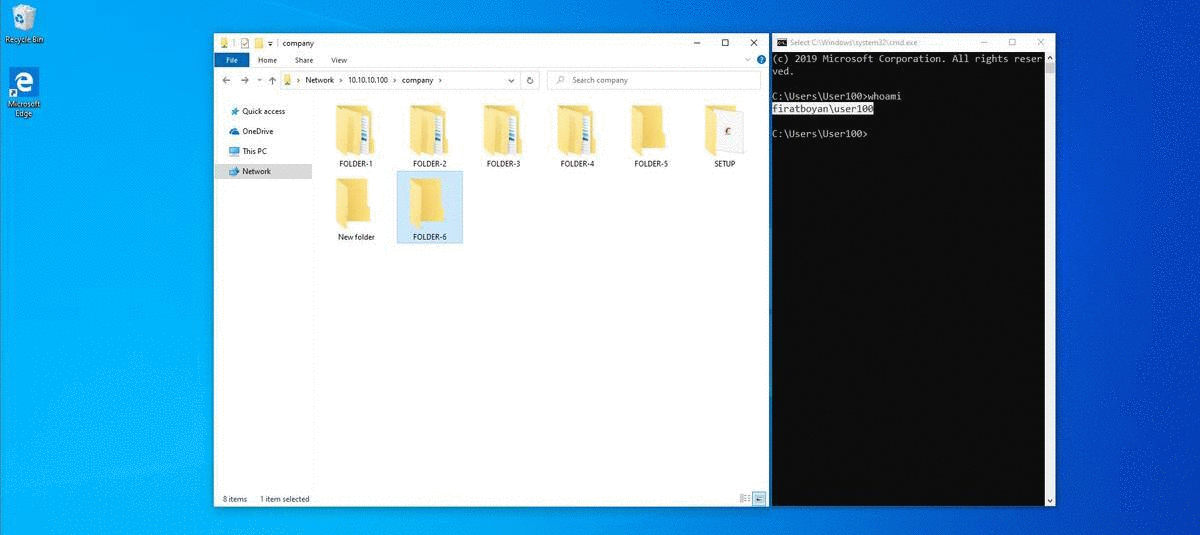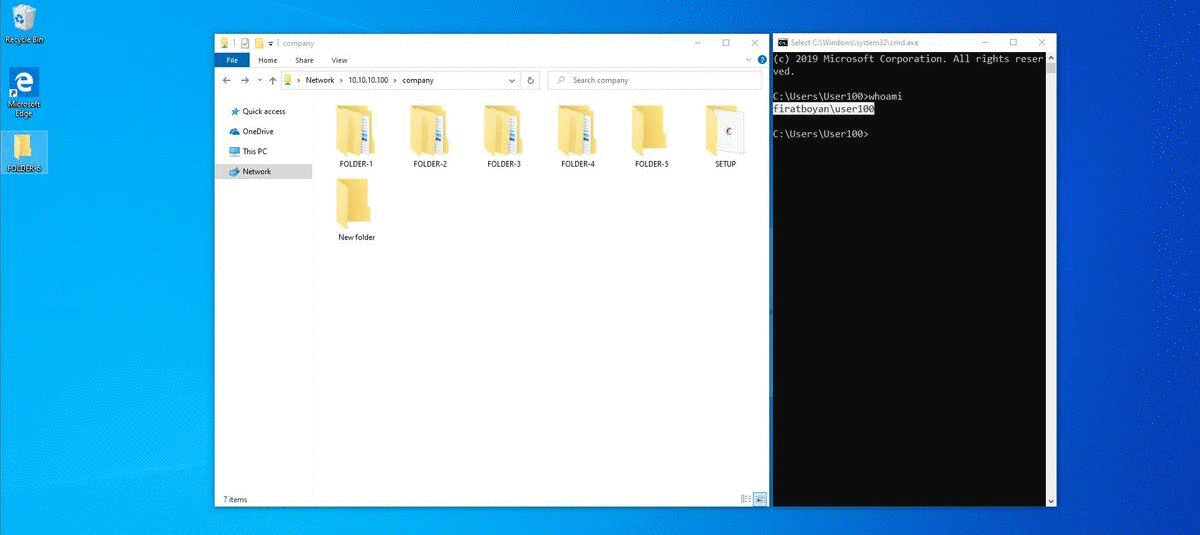
3- I mentioned that using Write permission alone cannot change the names of existing or newly created files or folders while in the allowed folder. This operation can be used to move folders or files from another directory (eg Desktop) to a shared folder (where the permission is defined), using Cut, Paste (paste) or Drag & Drop (drag & drop) method.
Application-3
1- I am updating the authority level on the Security Permission side to Modify in the same COMPANY folder for the same user, User100.
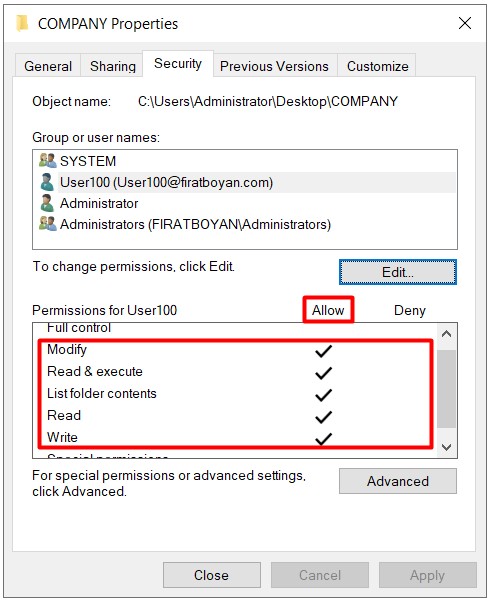
2- With the Modify authorization on the side of Security Permission (security-NTFS permission), the user now has the authority to change the name that covers all these, since he / she also receives the Delete authority. There are sometimes some people asking me which the advanced permissions (Advanced Permissions) correspoding to changing files or names is. Chaning a file or a folder names also means deleting, deleting the names. This is the logic.
Application-4
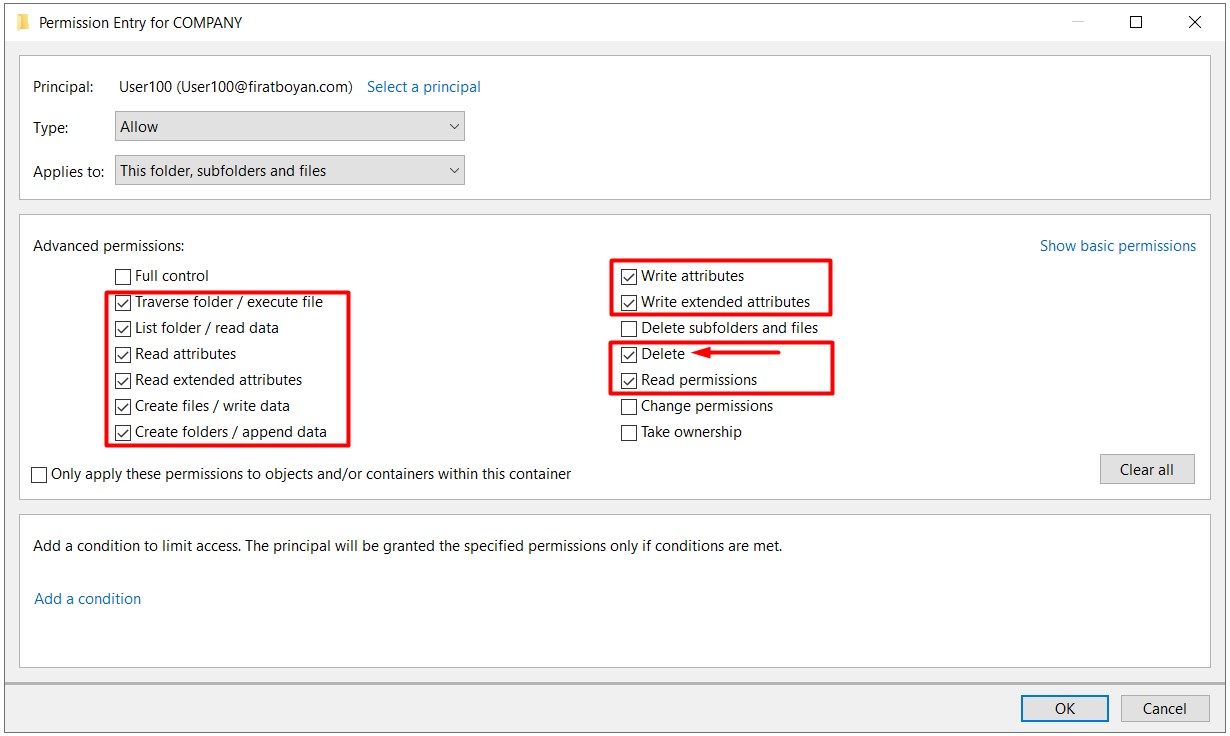
1- For the same user User100 in the same COMPANY folder, I am updating the authority level on the Security Permission side to Full Control.
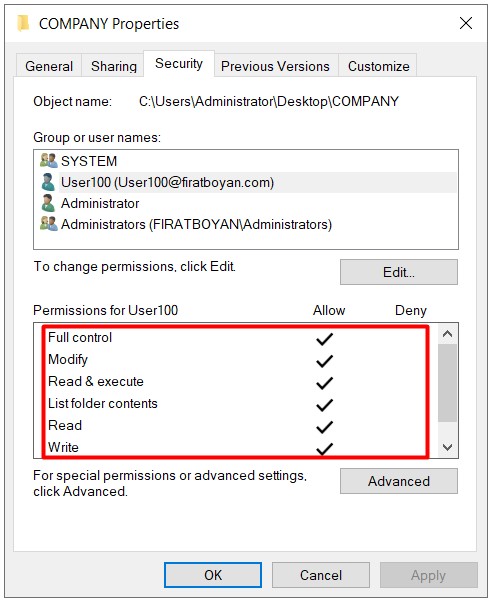
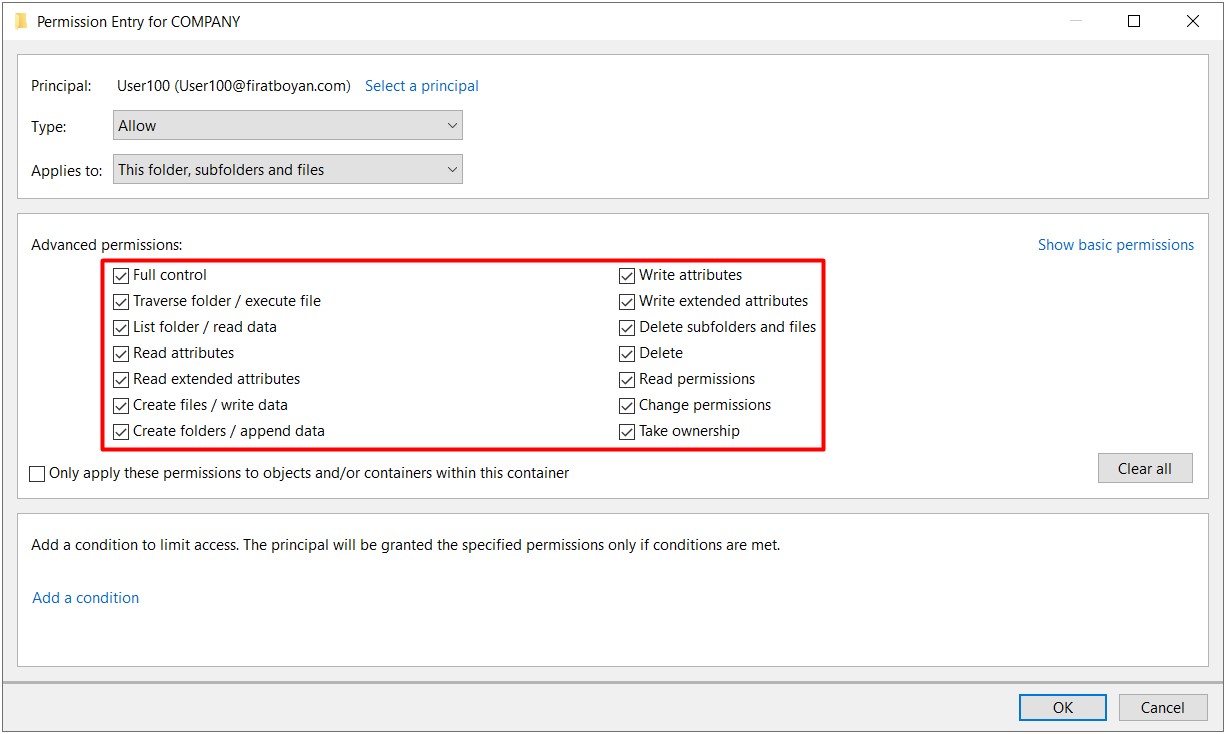
2- Although the user is given Full Control authority, he / she cannot benefit from the advanced permissions (Advanced Permissions) brought by the Full Control authority due to the Change restriction on the Security Permission (security-NTFS permission) side. Let me make it a little more detailed;
Both the Change authorization we grant for the Everyone user group on the Sharing Permission side and the Modify authorization we have assigned to the User100 user on the Security Permission side are equal in terms of the authorization level. I mentioned that the permissions on both sides (Sharing & Security) are compared and the most restrictive one is applied in the above parts of my essay. No matter which user in Active Directory you grant Full Control authority, this time since the most restrictive authority on the Sharing Permission side is Change, this permission will be valid and Full Control will be ineffective.
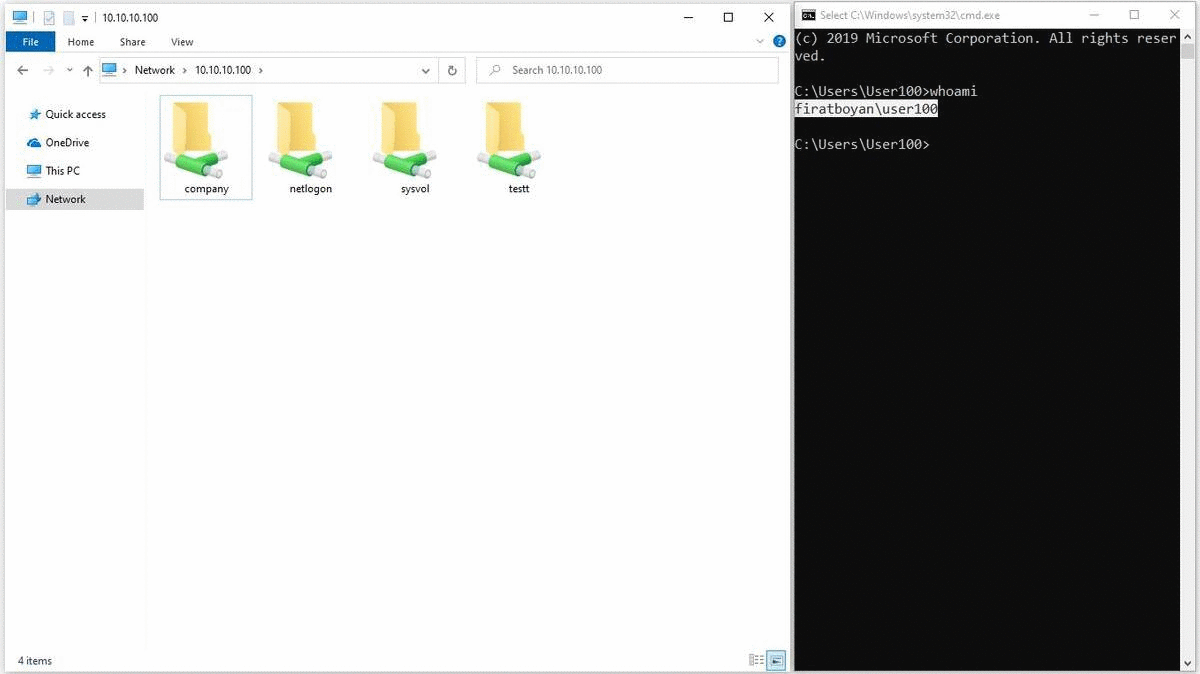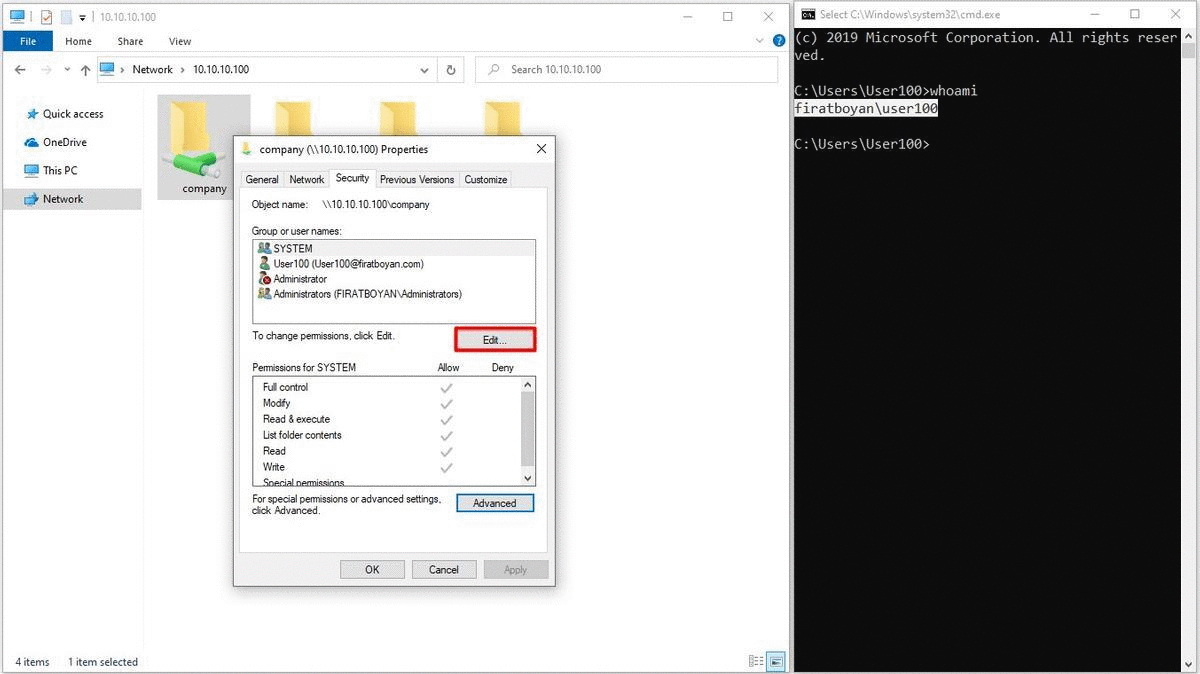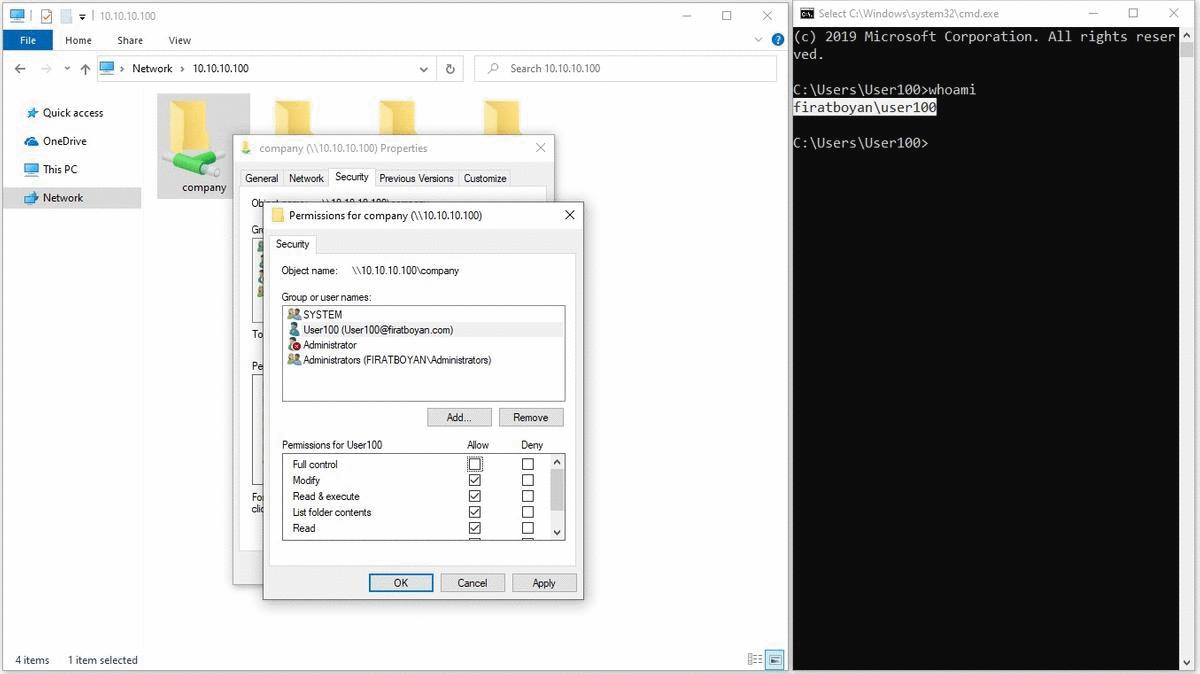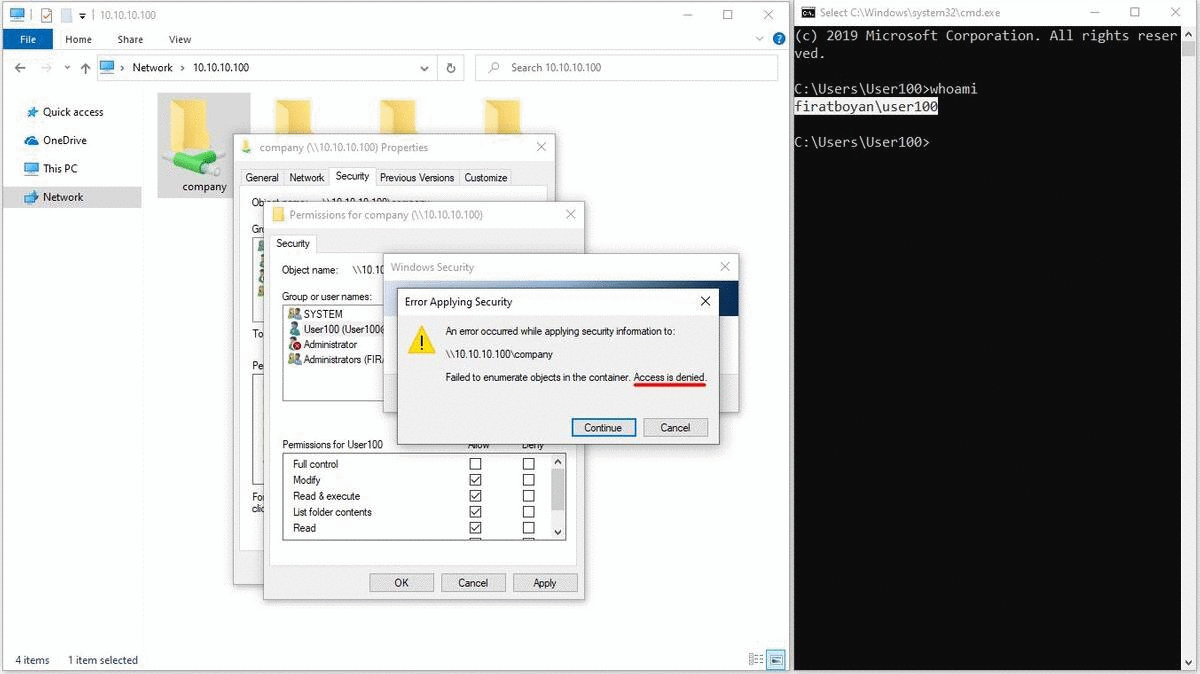
The Concept of Special Permissions
There are several Advanced Permission corresponding to each Basic Permission as I mentioned at the beginning of my essay. That is, each Basic Permission has the equivalent of several Advanced Permission in a group. When you disable one or more of the Advanced Permission corresponding to any Basic Permission, it is disabled as Special Permission.
Ex. When we remove Take Ownership from the Advanced Permission corresponding to the Full Control basic permission, it is turned off as Special Permission for the user.
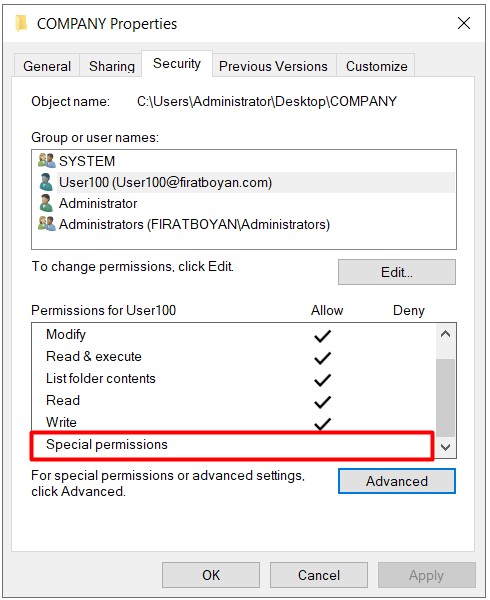
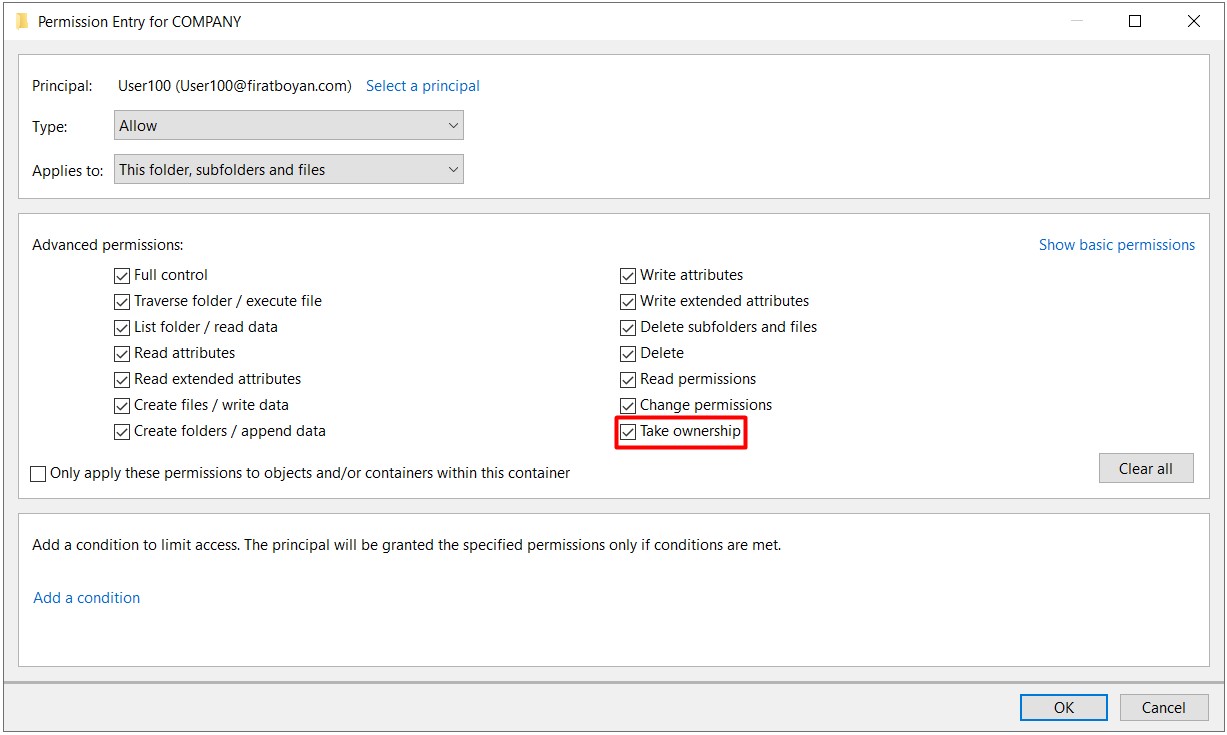
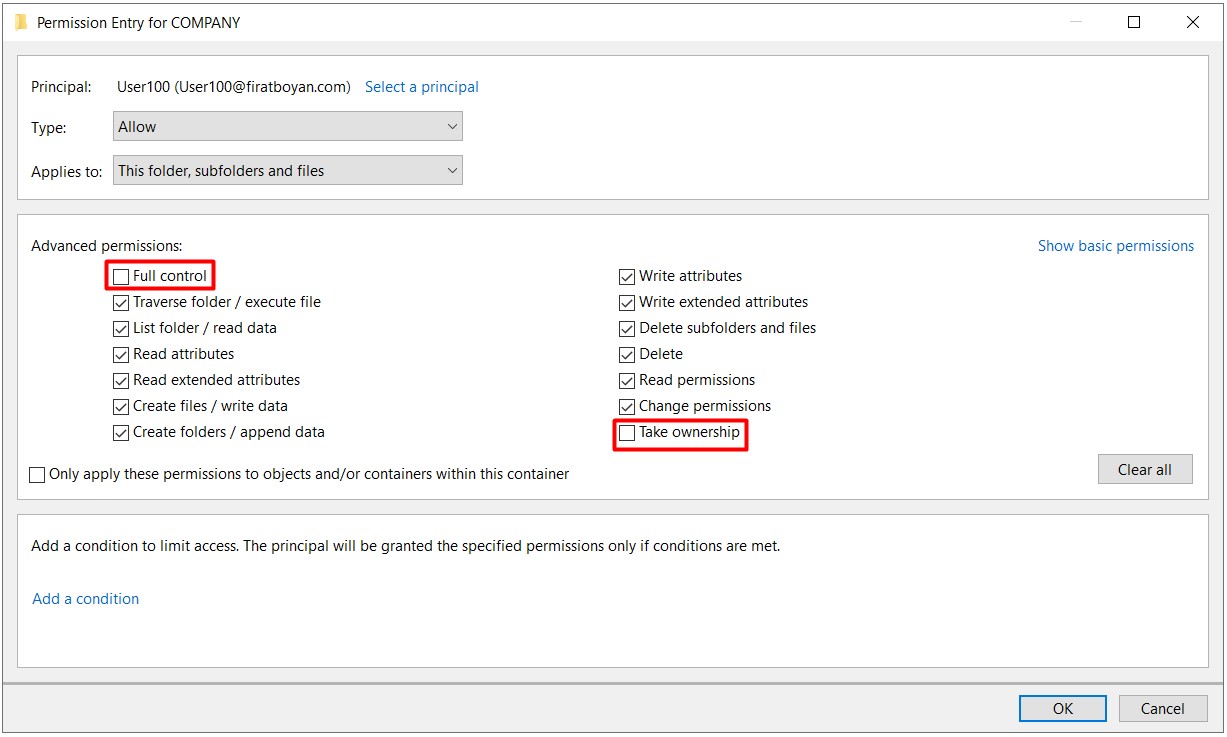
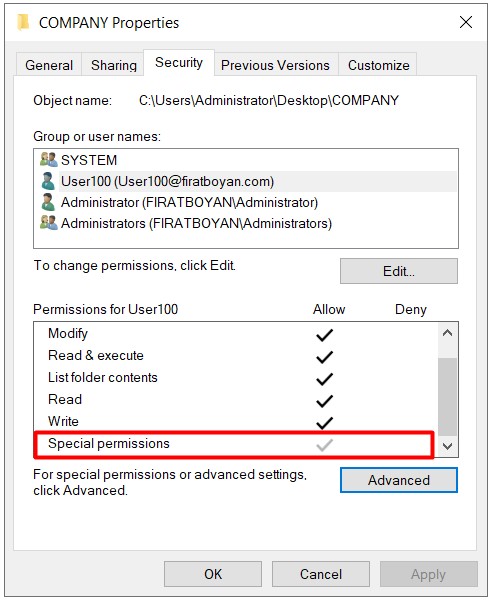
In summary, if you see Special Permission checked for any user or group in the ACL (Access Control List), this means that one or more of the advanced permissions (Advanced Permissions) of any Basic Permission are disabled.
The Concept of Inheritance
1- When you assign NTFS permissions to (a) user(s) or a group(s) in a folder, these permissions are automatically assigned to all subfolders and files by default.
When the authorization options of (a) user(s) or group(s) in the ACL (Access Control List) are in BLACK colour, it indicates that the authorizations are granted from that folder or the inheritance is disabled (Disable Inheritance).
On the contrary; when the authorization options of (a) user(s) or group(s) in the ACL (Access Control List) are in GRAY colour, it indicates that the authorizations derive from parent folder(s).
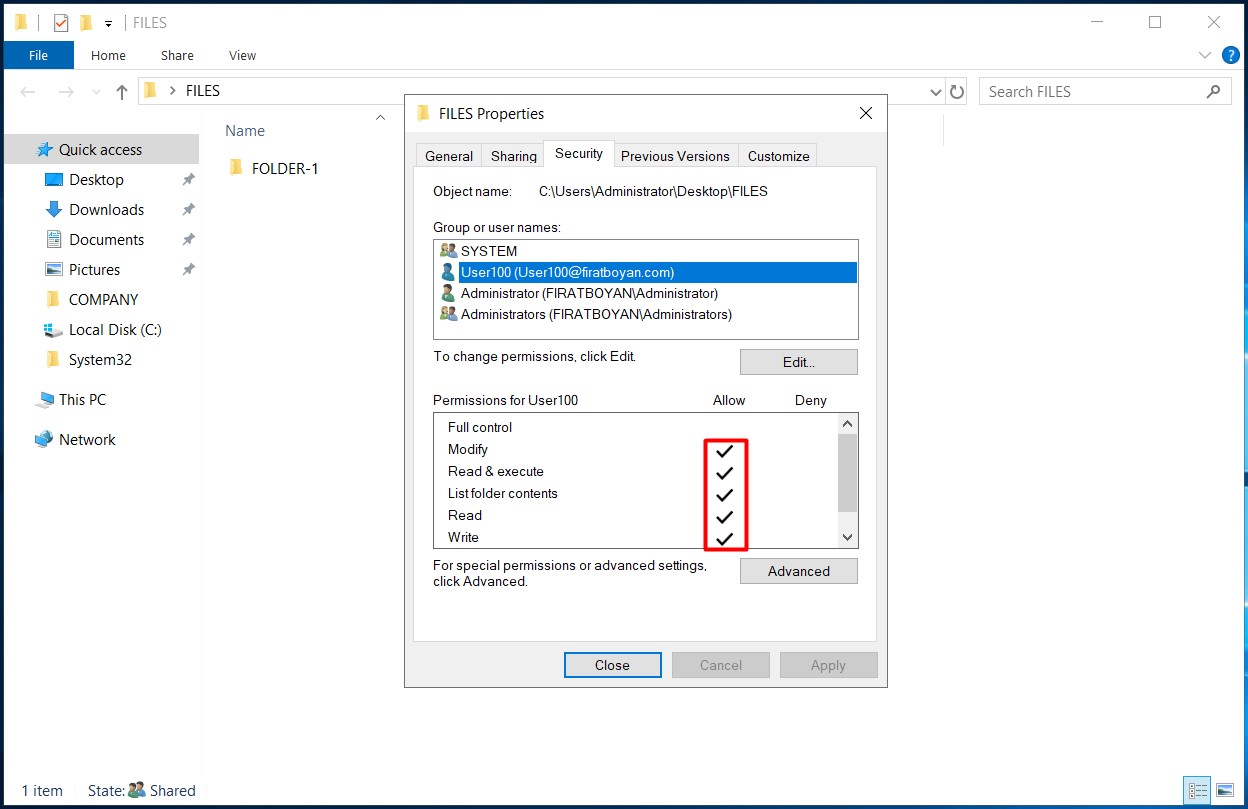
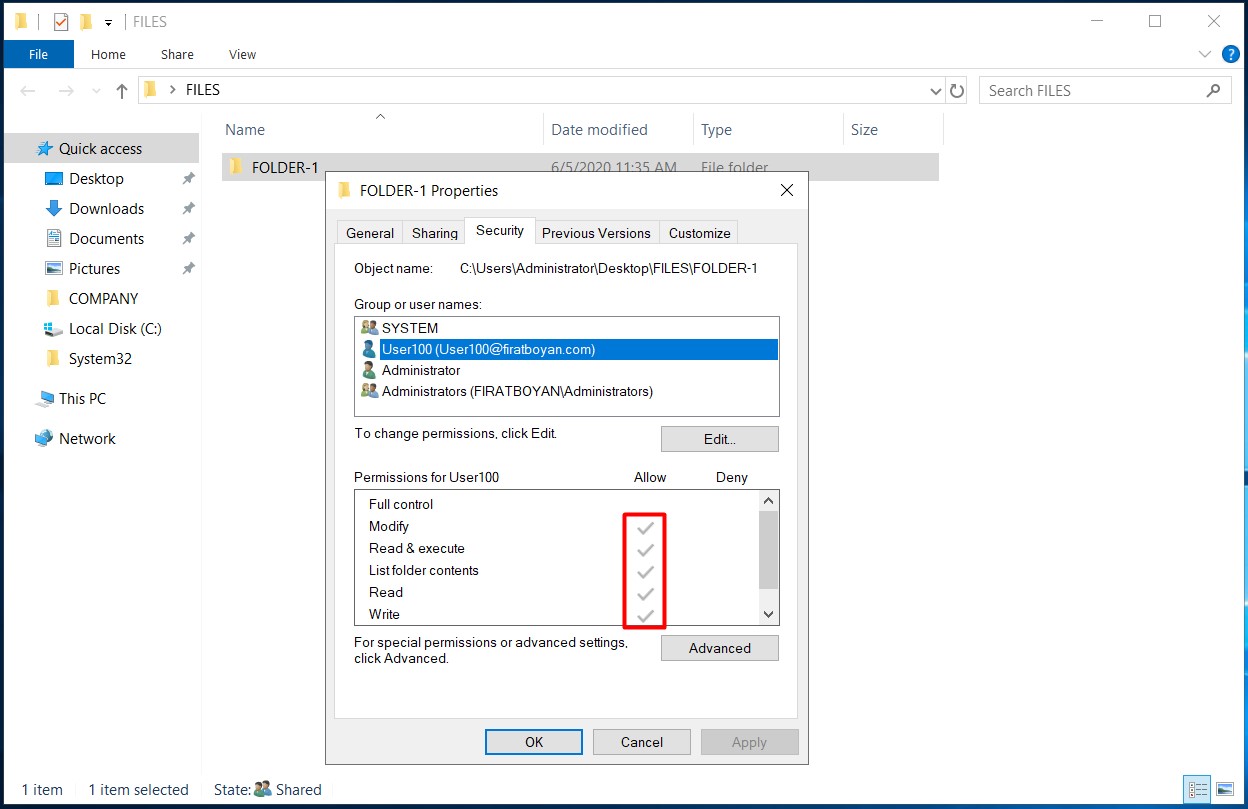
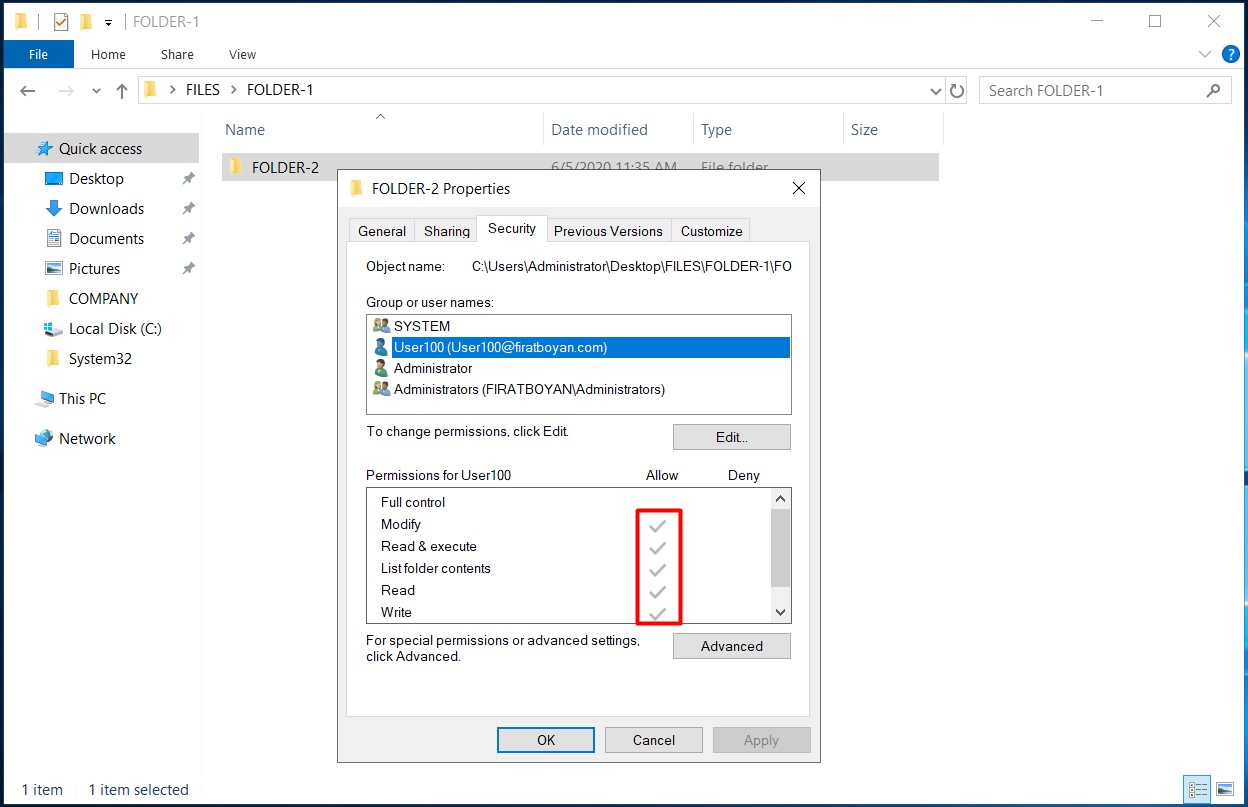
2- However, different authorization needs may arise for different users or groups in sub-folders. In such a case, the inheritance must be disabled (Disable Inheritance).
2.1- In order to disable the inheritance, I am clicking the Advanced button in the folder properties.
2.2- I am clicking on the Disable inheritance button at the bottom of the Advanced Security Settings window that pops up.
2.3- When I click on the Disable inheritance button, I see two options.
These are;
● Convert inherited permissions into explicit on this object: Current user(s) and group(s) are kept as they are in the ACL (Access Control List) and modification (deletion, correction of permissions) becomes available when canceling the inheritance with this option.
● Remove all inherited permissions from this object: Current user(s) and group(s) are completely deleted from the ACL (Access Control List) when inheritance is canceled, and it is allowed to make changes (add, delete, correct permissions) from scratch with this option. The only difference with this option is that users and groups are not completely deleted in the ACL (Access Control List). I suggest you be careful when choosing this option.
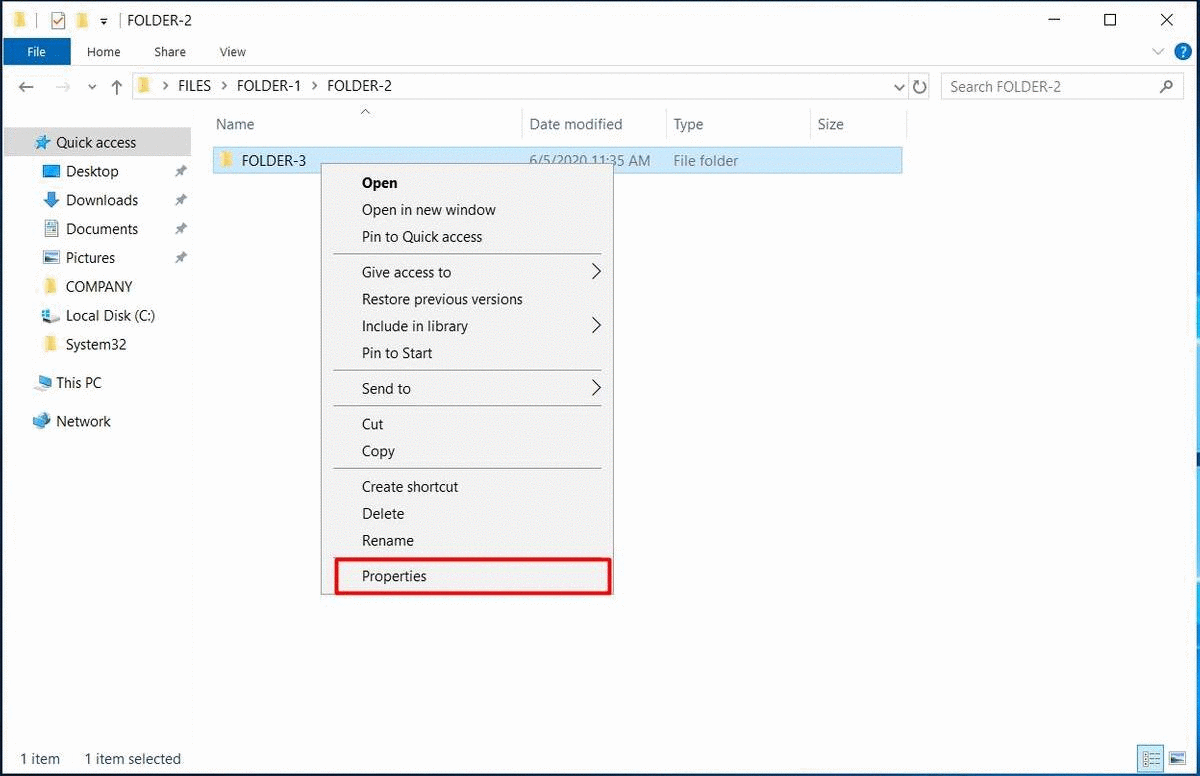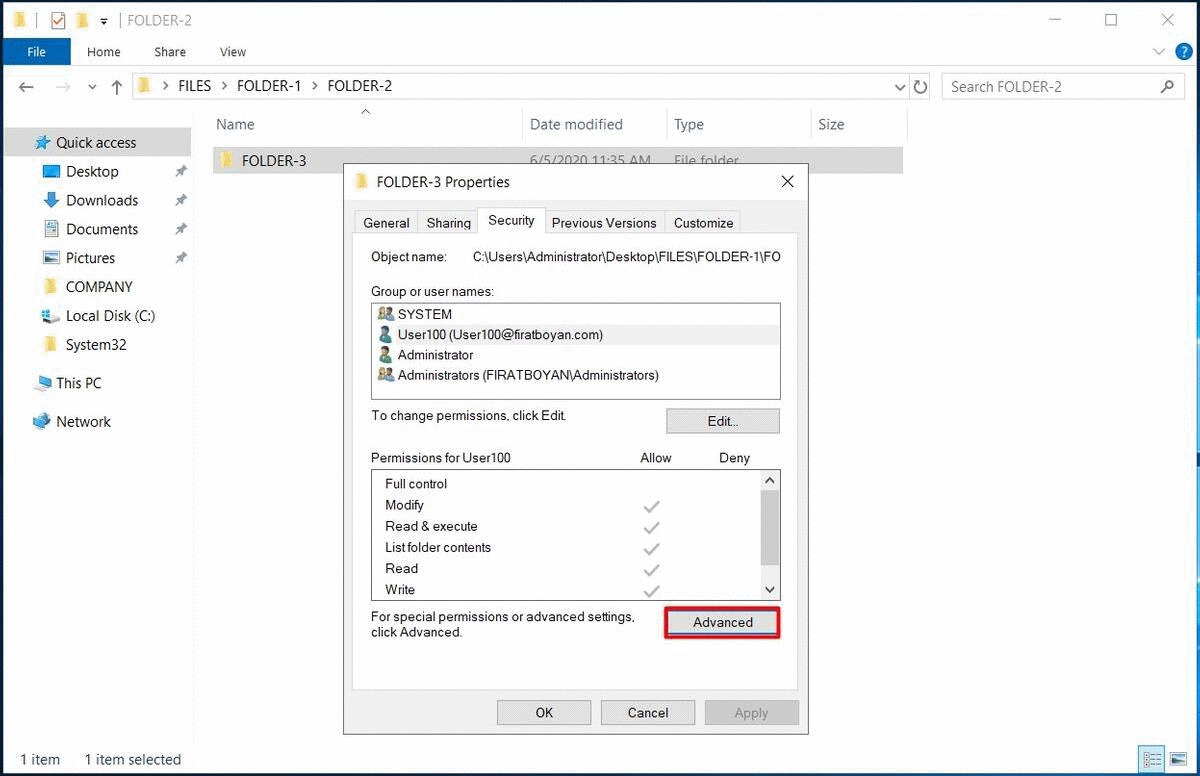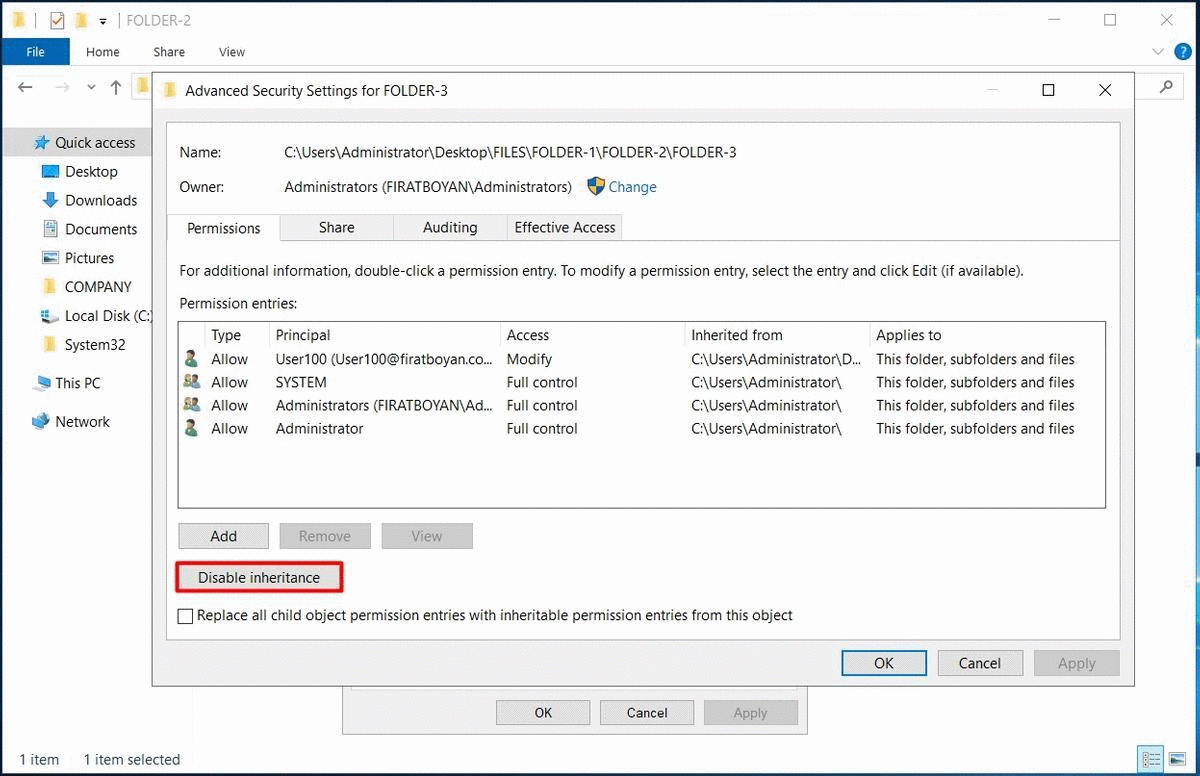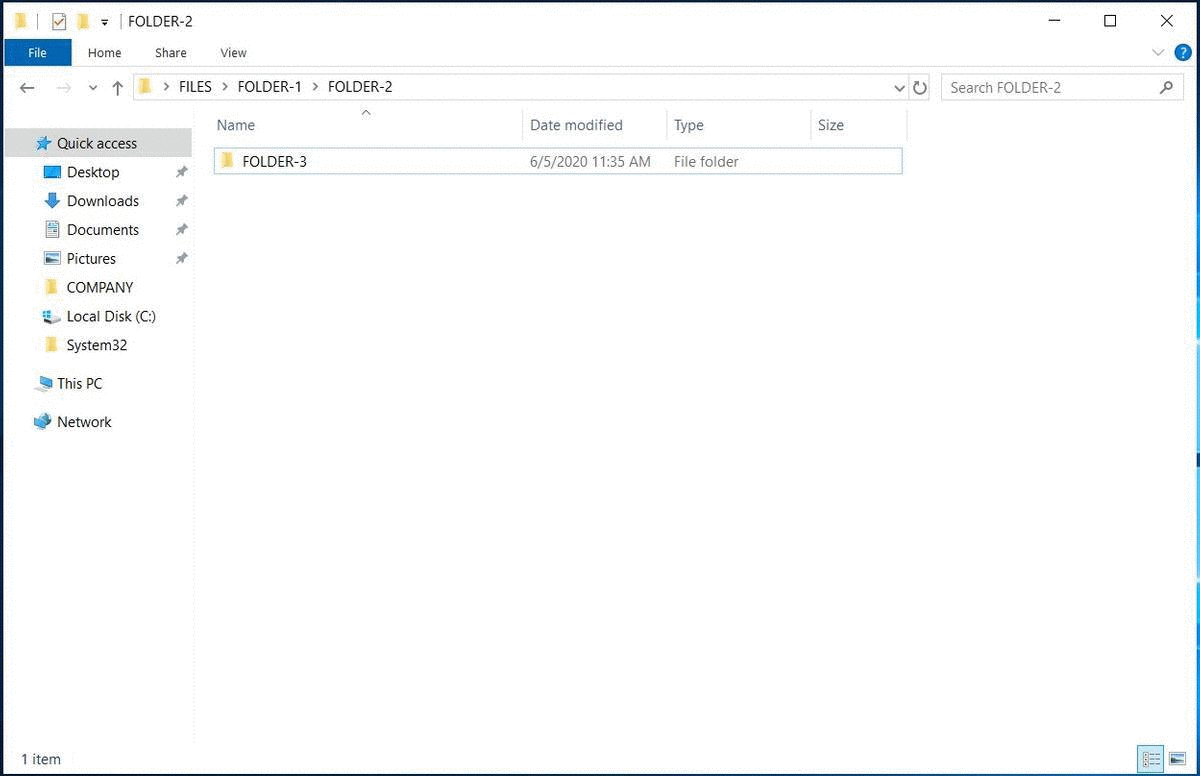
The Comparison of Permissions Restructuring
The comparison of permissions on a folder or folders and that they become unmanageable is a common situation that I often encounter in organizations I consult. In the authorizations that are tried to be managed unplanned and unconsciously, things can become seriously intractable.
So what do we do in such a situation?
In this case, the Replace all child permission entries with inheritable permission entries from this object option applies the same permissions to the subfolders in the folder where the option is selected (even if inheritance is disabled in the subfolders!).
1- I am choosing a parent folder to edit the permissions for.
2- I am clicking on the Advanced button in the folder properties window.
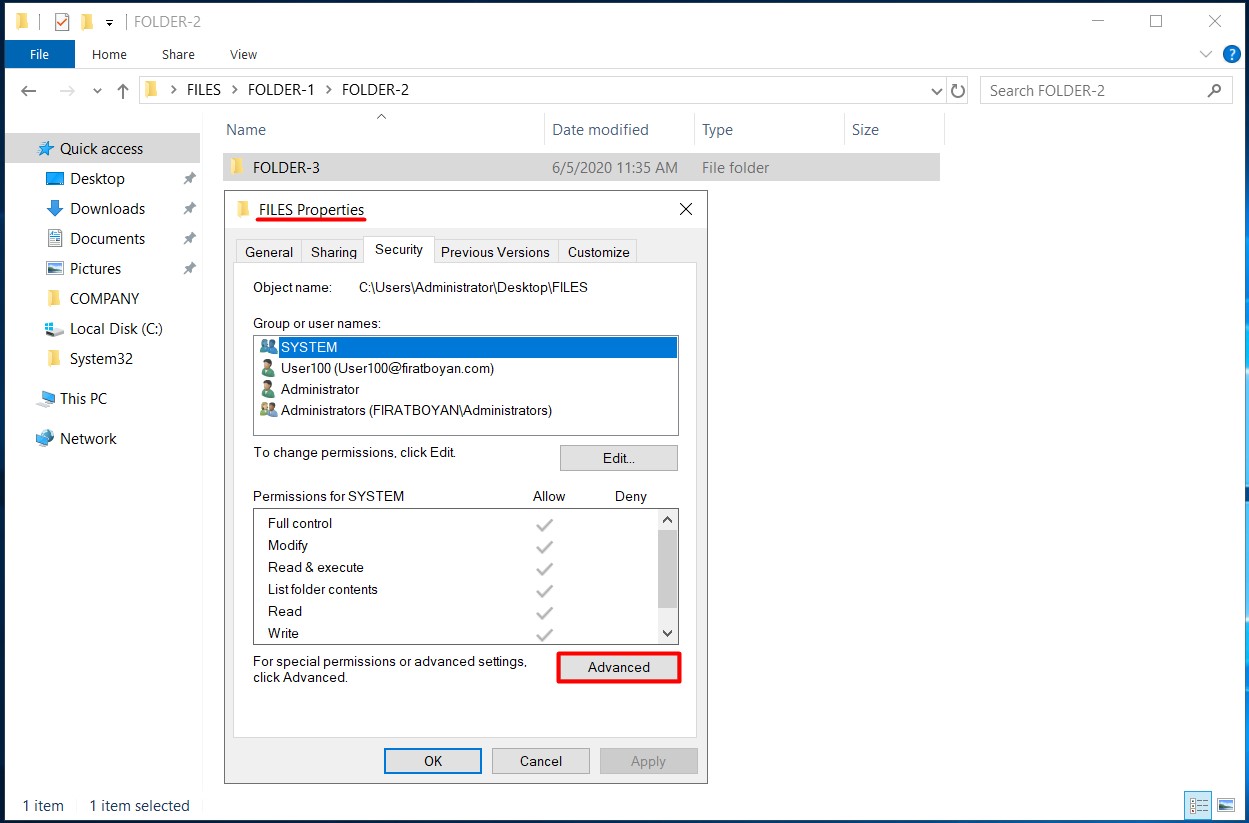
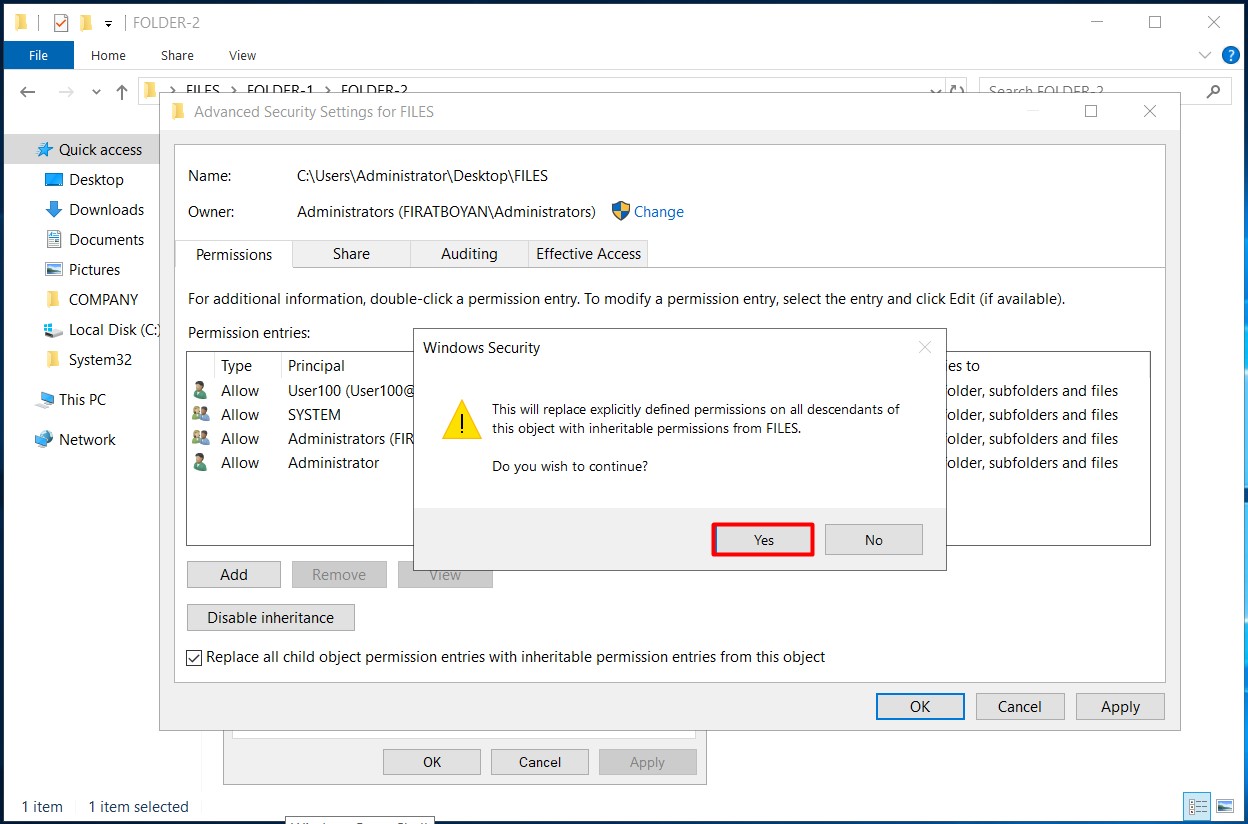
3- I am selecting the Replace all child permission entries with inheritable permission entries from this object option at the bottom of the Advanced Security Settings panel in the folder that comes up and completing the process by clicking on the OK button.
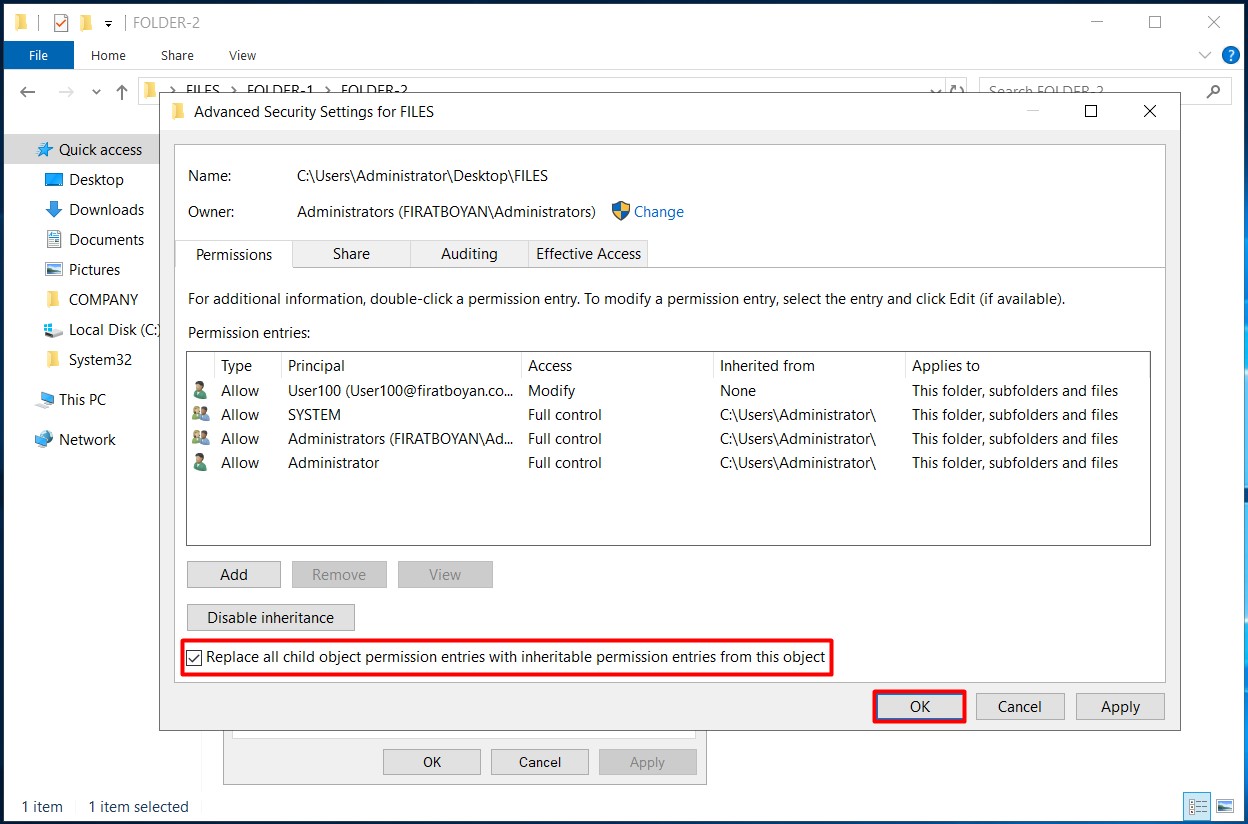
4- I am geting a warning stating all permissions in this folder will be applied to subfolders. I am clicking on the Yes button.
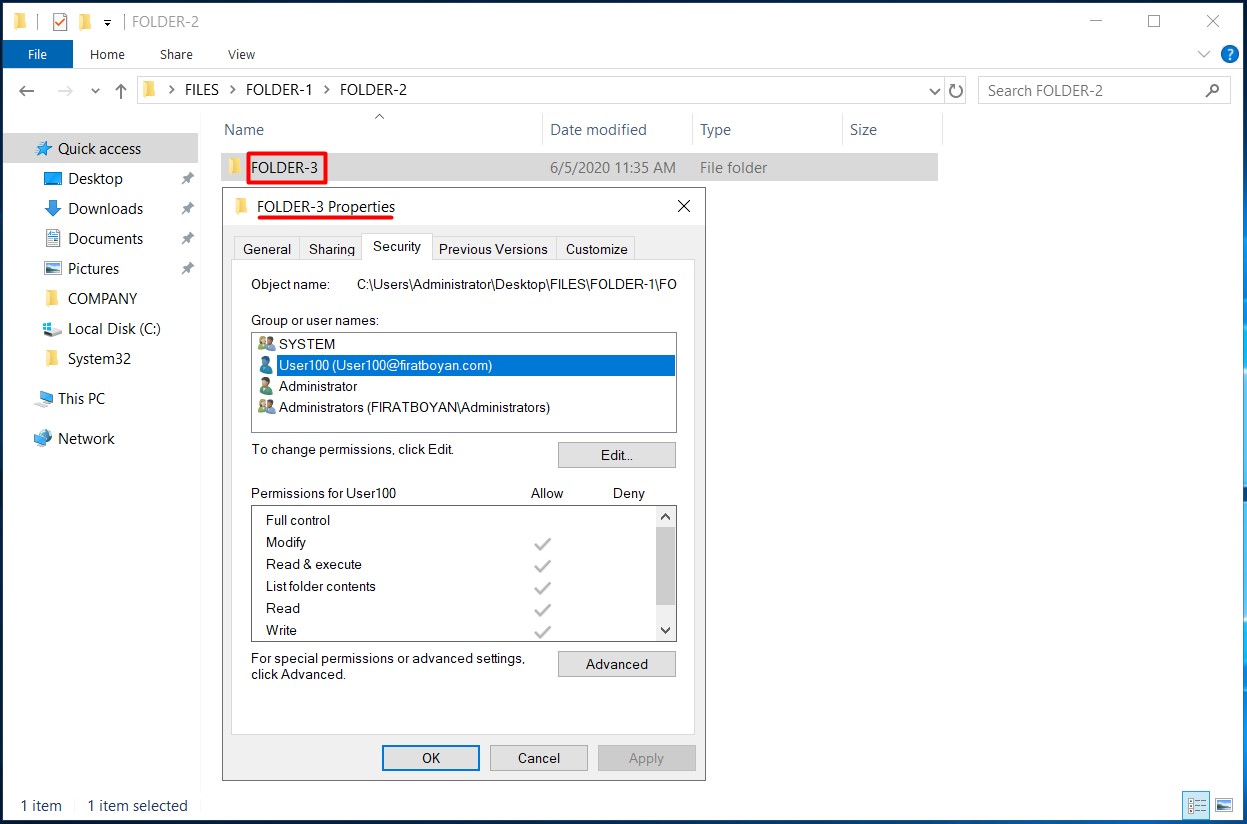
5- We disabled the inheritance in the FOLDER-3 folder under the FILES main folder. The authorizations in this folder were arranged according to the folder where I selected the Replace all child permission entries with inheritable permission entries from this object option, and inheritance was reactivated.
Folder Ownership concept
By default, the owner of a folder is the one who created that folder. Although Folder Ownership may seem insignificant in practice, it is important in many ways:
According to this;
• To create a Mandatory Profile on the Roaming Profile, folder ownership is required to access the Roaming Profile (roaming profile) folders.
• In Disk quota operations created with File Server Resource Manager (FSRM), Disk quotas are calculated according to folder ownership. For this reason, each user must take the ownership of the folder to himself.
• The SID + RID number information remains in the Folder ownership of a User whose account is deleted from Active Directory. In such cases, the folder must be migrated to an active Active Directory User.
• Even if the owner of a folder only has Read permission on the associated folder, the folder ownership gives the right to manage the permissions in the ACL (Access Control List).
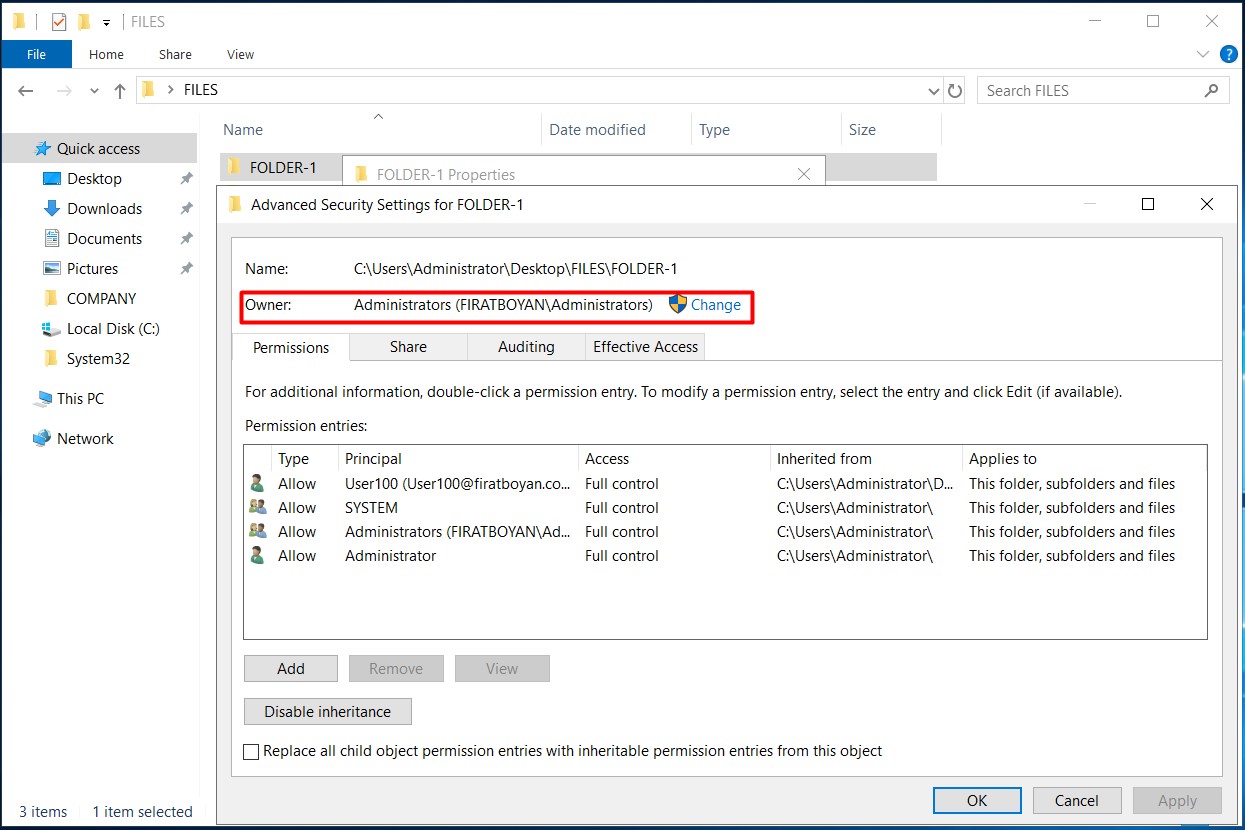
6- We can see that the folder owner (Folder Owner) of the folder named FOLDER-1 under the main folder named FILES is the Administrators user.
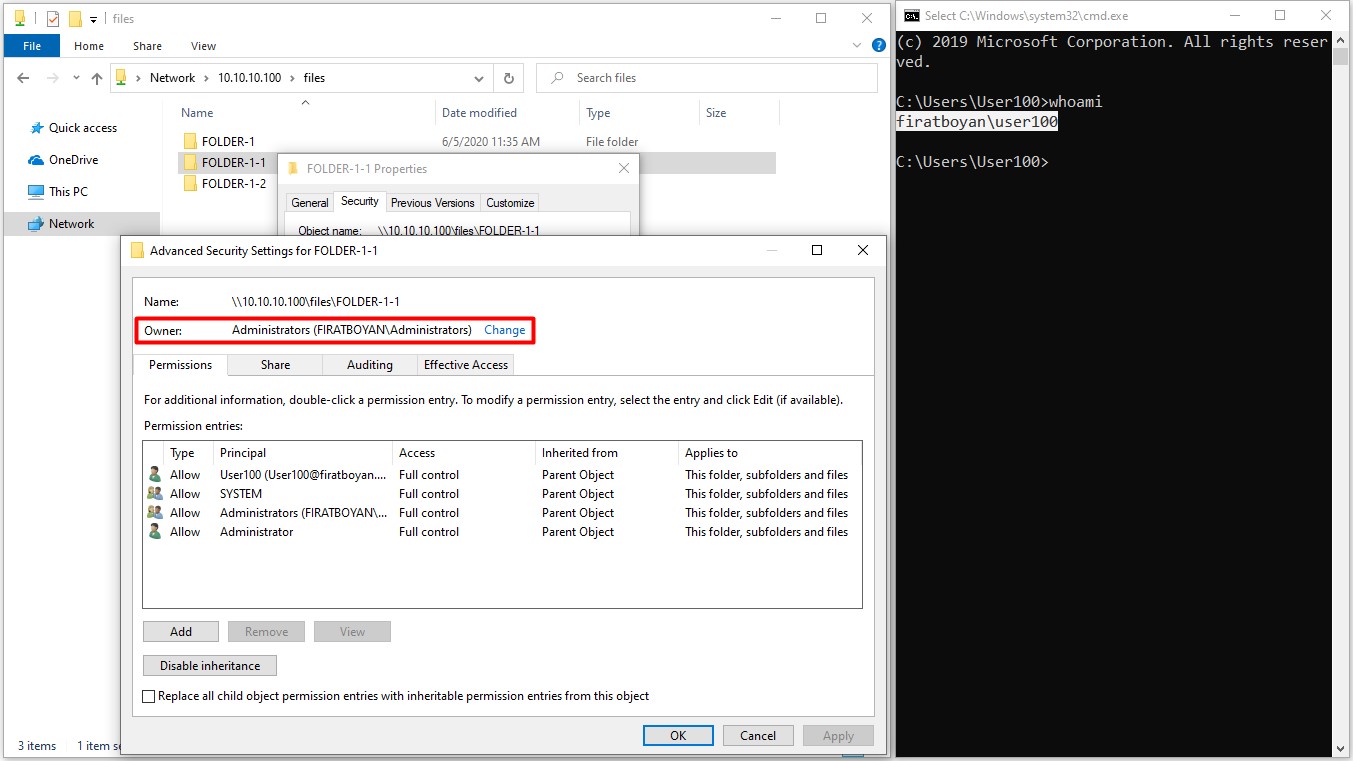
6.1- When the Administrators user opens another folder named FOLDER-1-1 under the FILES main folder, the folder owner (Folder Owner) automatically becomes an Administrators user.
6.2- When user User100 opens a folder named FOLDER-1-2 under the main folder of FILES, this time the folder owner (Folder Owner) automatically becomes User100. Info !: By default, the owner of a folder is the one who created that folder.
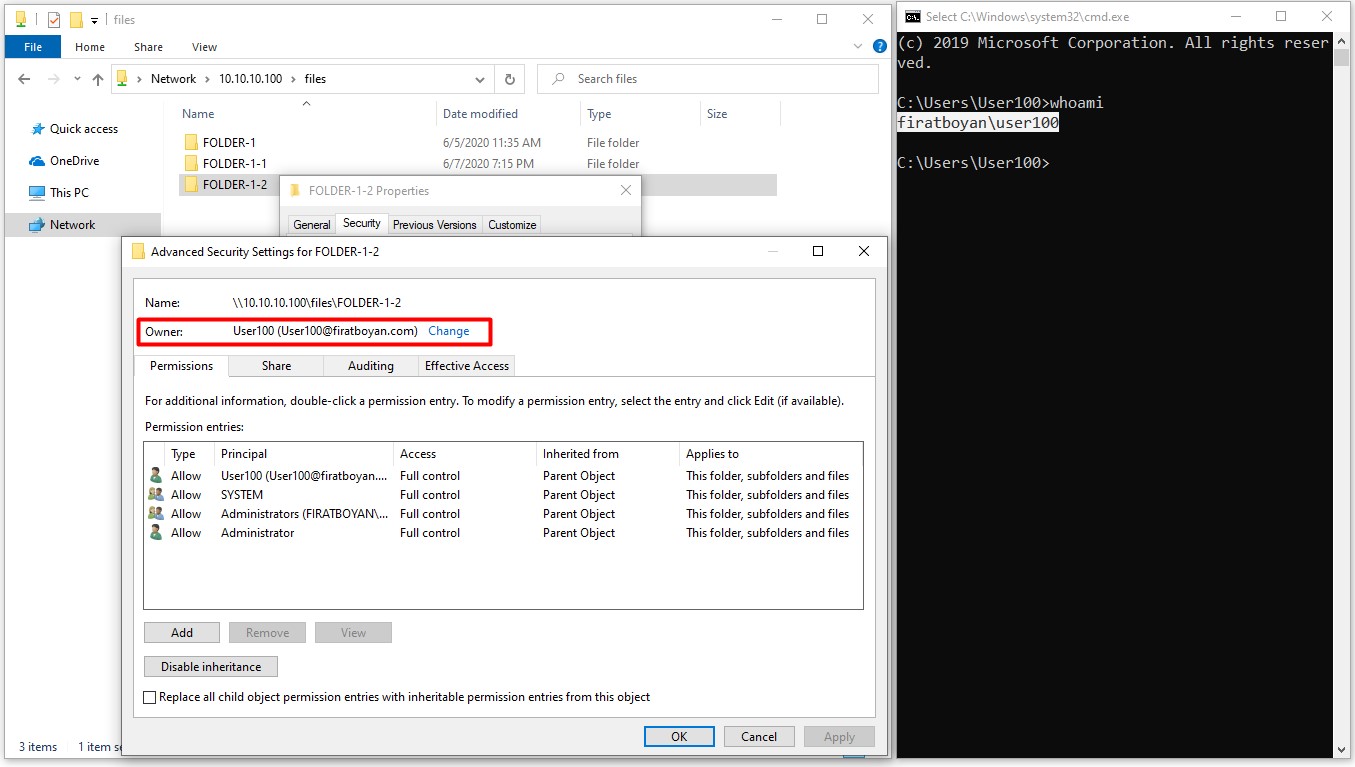
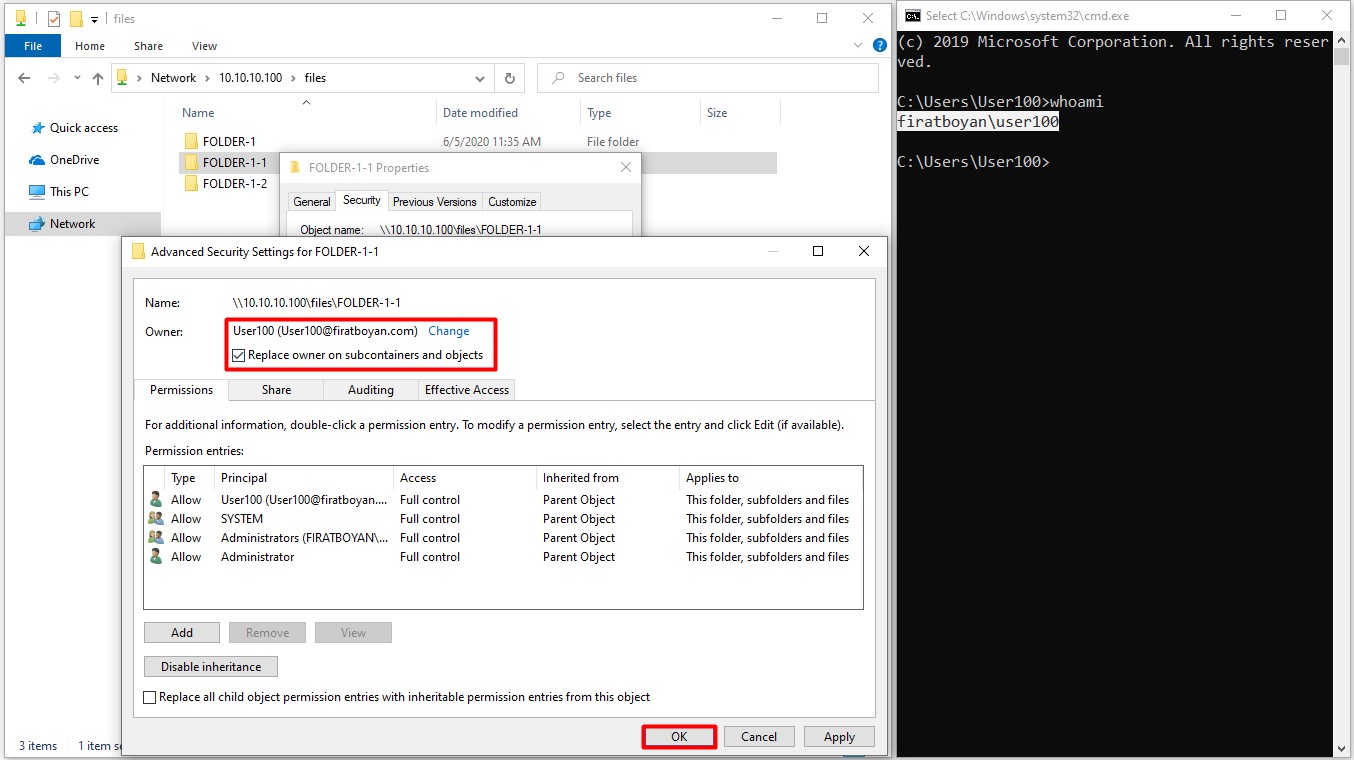
6.3- When the user User100 wants to take ownership of the folder named FOLDER-1-1 under the FILES main folder, which the folder owner (Folder Owner) is Administrator, it is sufficient to click on the Change link and specify the user to assign the folder ownership.
NOTE 9: The user User100 must have Take Ownership advanced permission (Advanced Permission) based on the Full Control basic permission on the folder in order to perform this action.
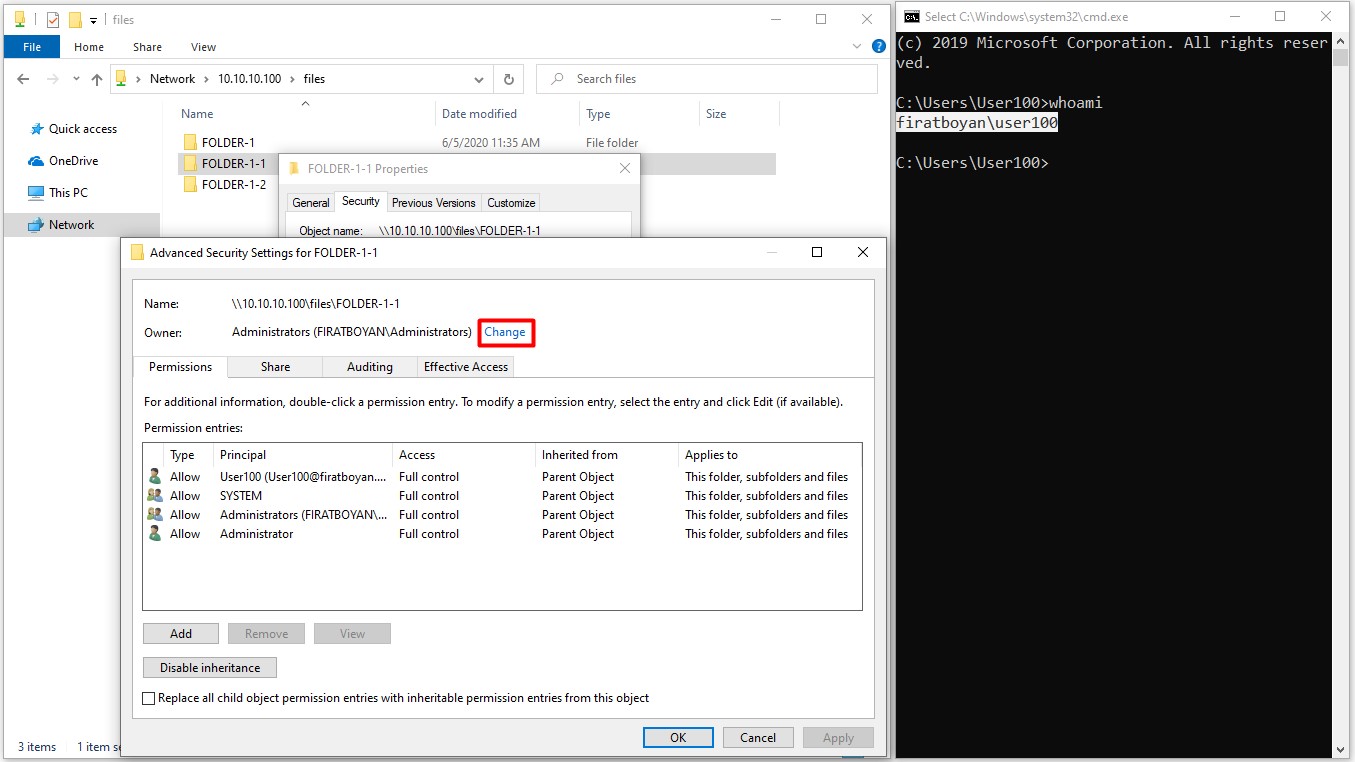
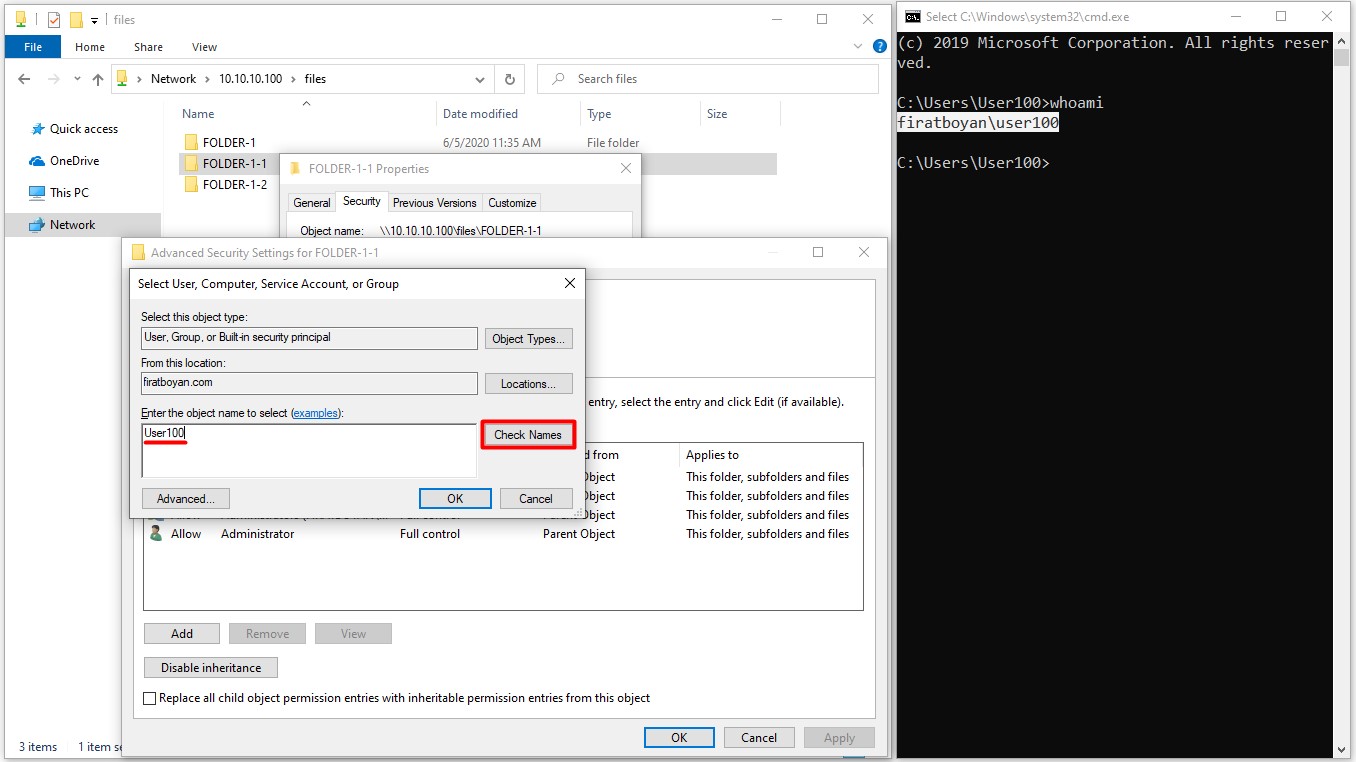
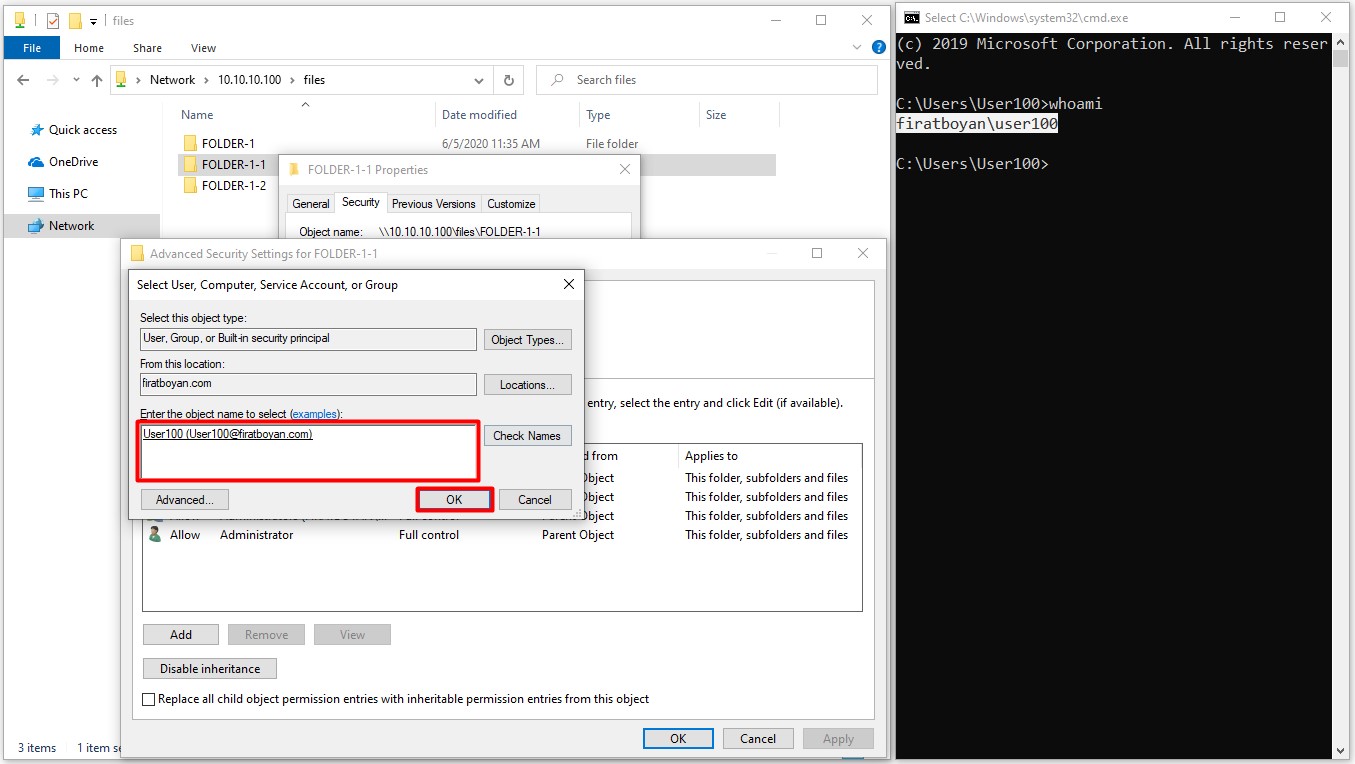
6.4- When you click the Replace owner on subcontainers and object option at the bottom, the folder ownership (Folder Ownership) in the subfolders will be transferred to the user in the main folder where the ownership has been taken or transferred upon taking or transferring the ownership of the folder.
NOTE 10: Any user or group that has Take Ownership permission from the Advanced Permissions on the relevant folder can take over the folder ownership.
I hope it benefits...
You may submit your any kind of opinion and suggestion and ask anything you wonder by using the below comment form.